testimonials
What Our Customers Are Saying…
Digital Adoption Platform

Monday.com



















Your IAM Systems Are Vulnerable
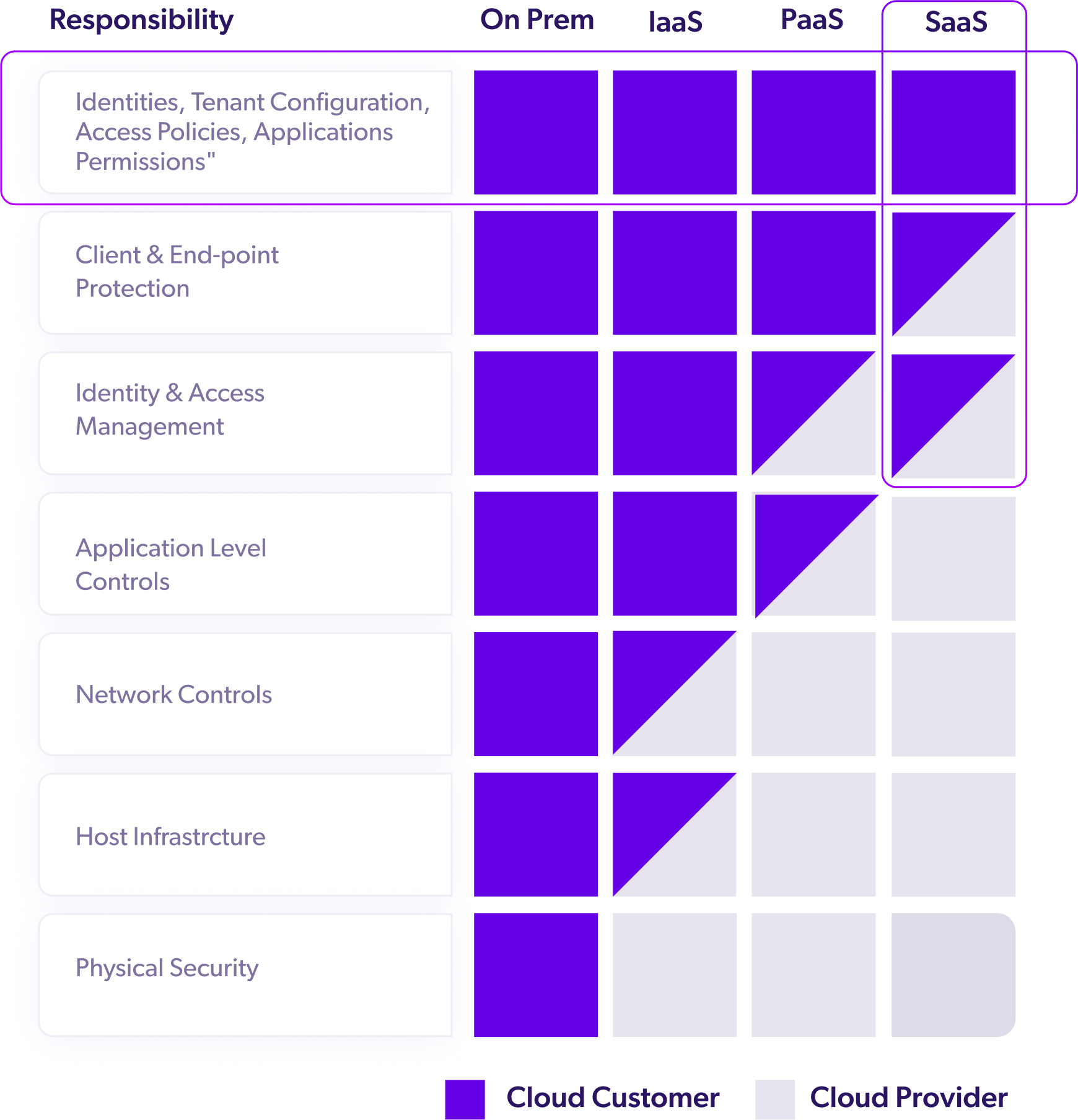
Shared Responsibility
Customers are responsible for securing what they host in IAM systems and mitigating risks of misconfiguration, deletion, and tampering.
Human Error
Misconfigurations may cause downtime, lengthy manual recoveries, and unauthorized access, or block legitimate users.
Ransomware
Compromised IAM systems present a substantial threat to both availability and security, leading to significant operational and financial risks.
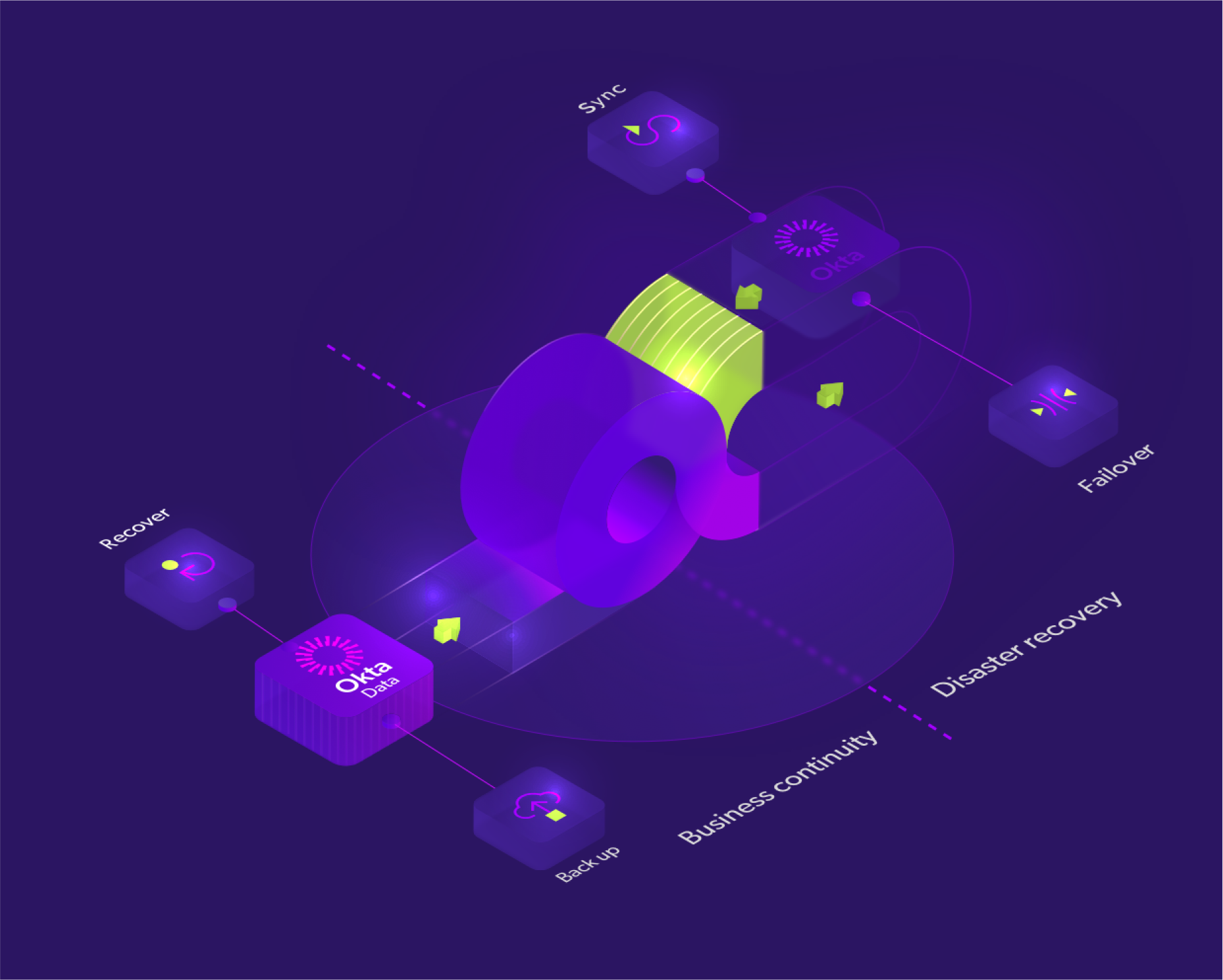
Is Your Okta Tenant Truly Recoverable?
Explore insights into the recoverability of your Okta tenant with Acsense.

Why Acsense?
Prevent Business Disruption
Ensure your people and customers always have access to the apps they need—avoiding costly downtime and lost productivity.
Protect Revenue & Reputation
Recover your IAM infrastructure in minutes, minimizing customer and employee downtime costs —keeping your bottom line healthy.
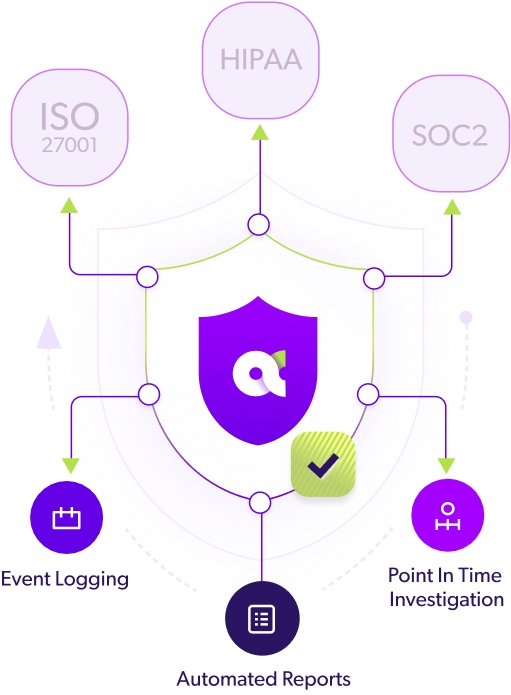
Reduce Compliance Risk
Have audit-ready recovery proof of your IAM at your fingertips—cutting hours of prep work and reducing the risk of penalties.
Use cases
Business Continuity
Unmatched protection against identity downtime.
Learn More >>
Ransomware Recovery
Continuous IAM uptime with automated recovery.
Learn More >>
Compliance
Simplified IAM compliance at scale.
Learn More >>



Use cases
Business Continuity
Our proactive continuity features support Business Continuity teams, maintaining high availability and operational stability amidst IAM breaches, insider threats, or misconfigurationsLearn more >>
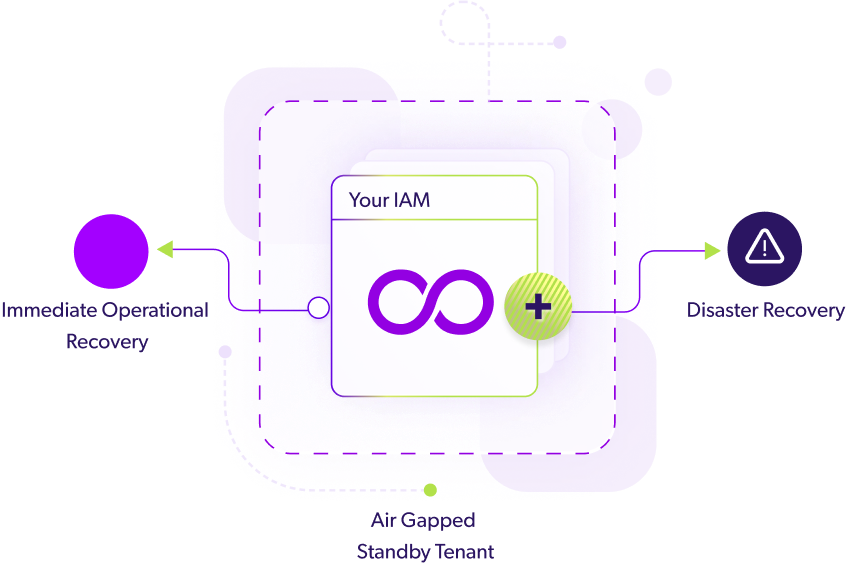
Disaster Recovery
Mitigate Okta downtime using a ready backup tenant for Disaster Recovery. Eradicate extraneous costs tied to complex recovery processes and downtime!Learn more >>
Governance Risk & Compliance
Real-time change monitoring enhances your Compliance and Risk teams' IAM compliance, security, and resilience, ensuring robust and compliant business operationsLearn more >>

What's in it For You?
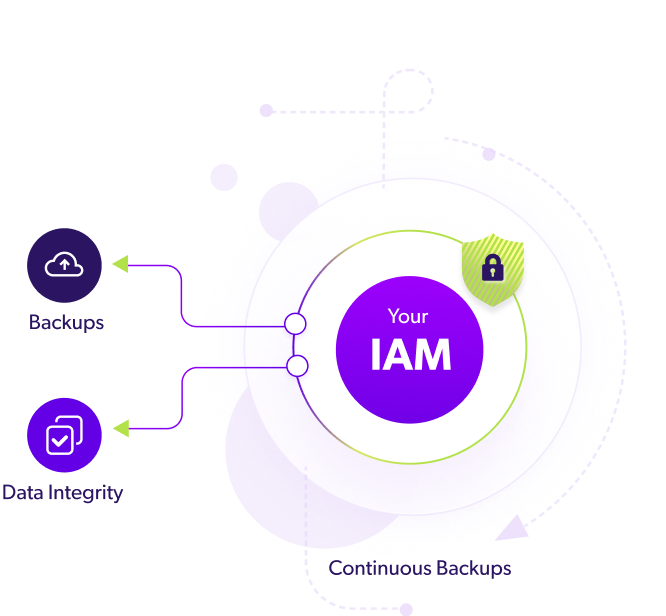
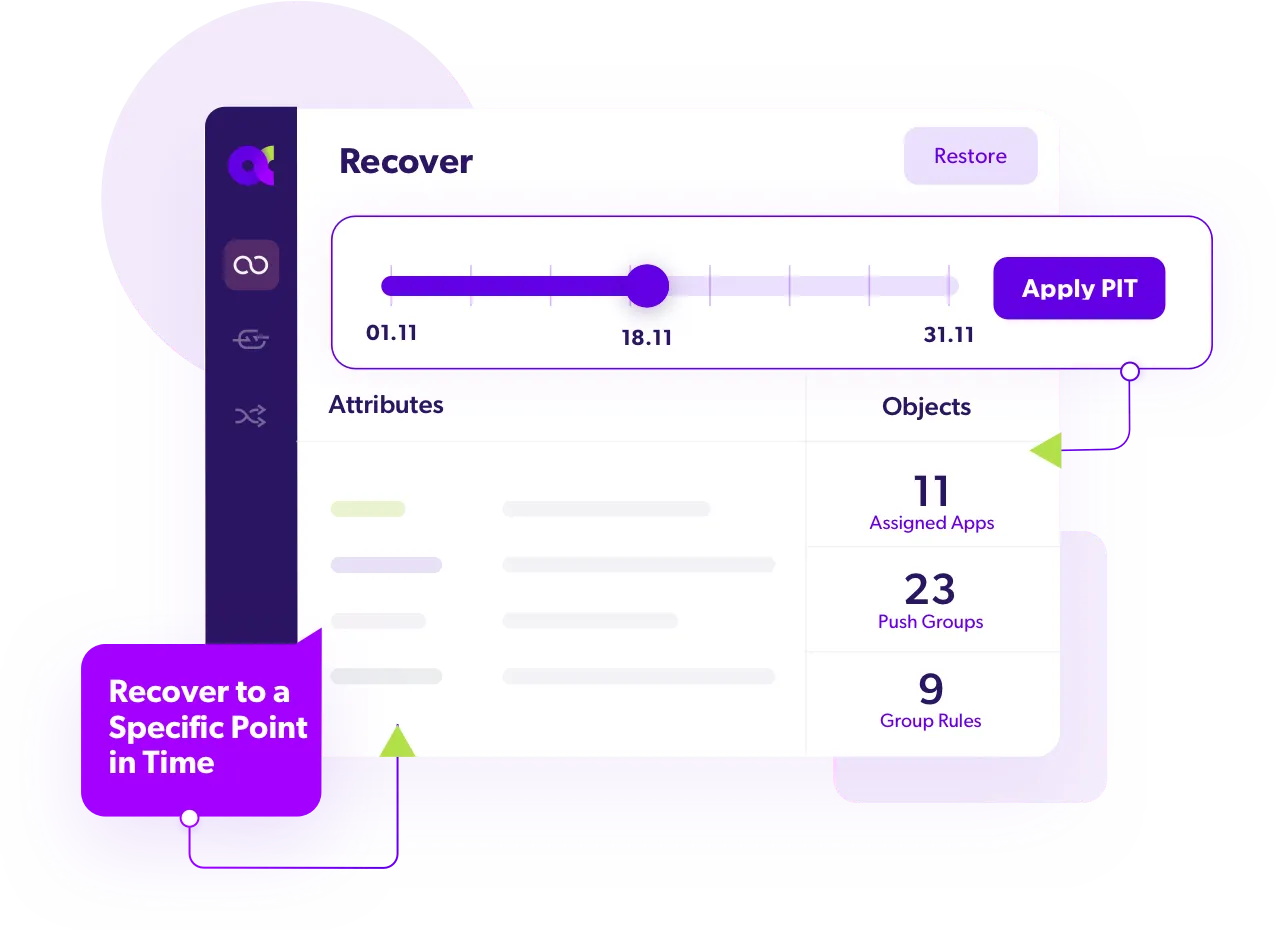
01. Continuous Data Protection
Seamlessly synchronize your IAM tenant in a secured, air-gapped environment, providing continuous protection for all your data and configurations.
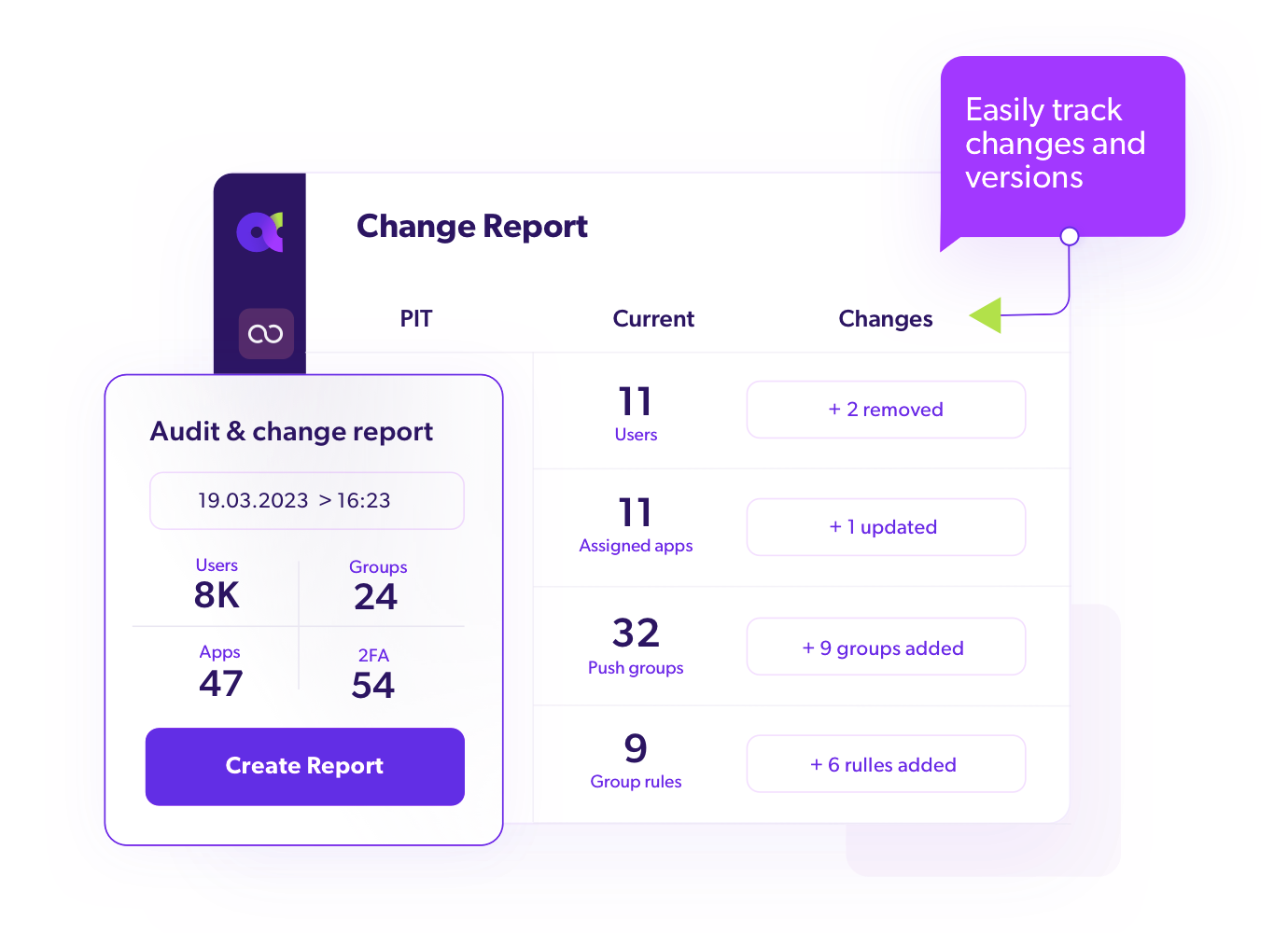
02. Monitor Changes
Assess your IAM posture and recoverability by reviewing configuration changes and object activity between specific points in time.
03. Rapid Recovery
Choose any Point-in-Time (PiT) to effortlessly rollback minor data changes or fail-over to a secondary IDP.
The Okta Disaster Recovery Plan Guidebook

shared responsibility model
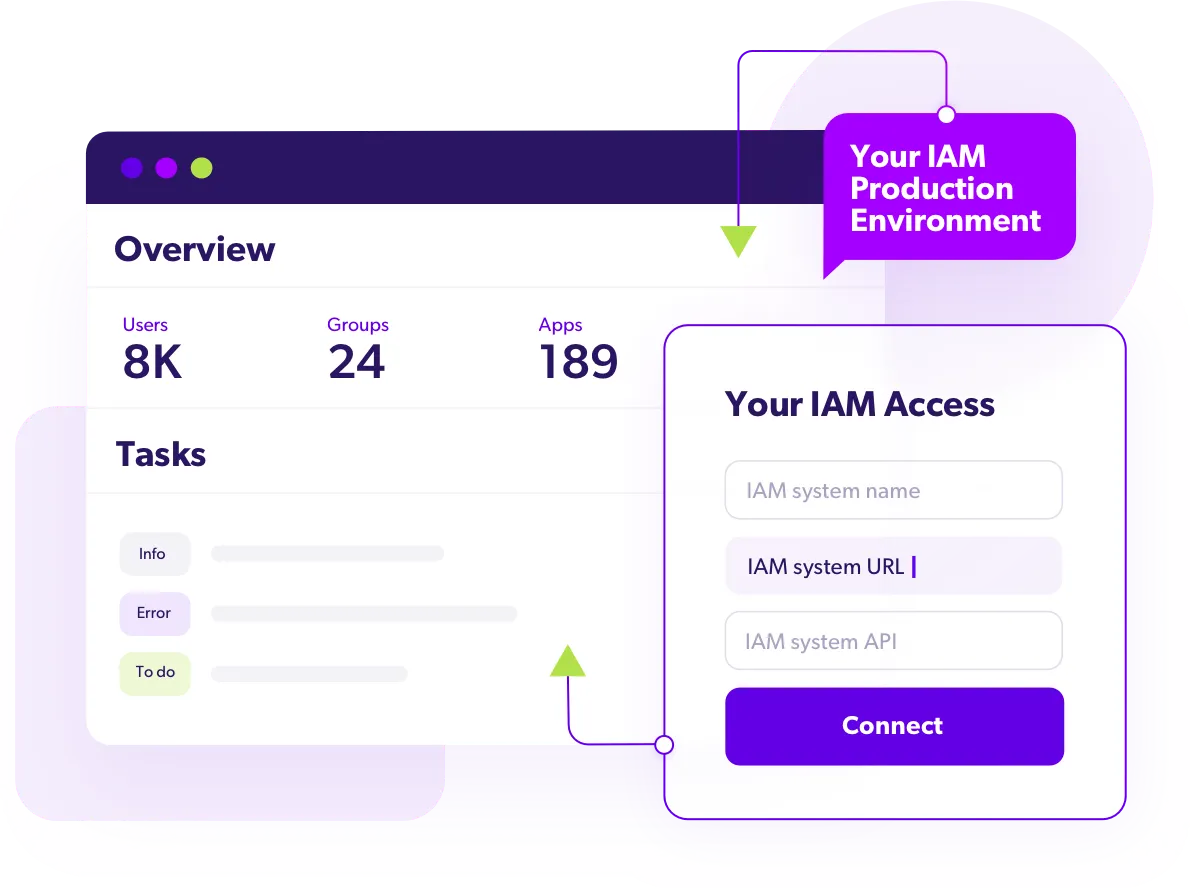
Take Back Control of Your IAM Data
Cloud providers, such as Okta, Azure AD, Ping and Forgerock rely on a shared responsibility model. In a nutshell, you are responsible for the information, configuration, rules, etc. that you define within your particular IAM configurations.
Protect Your IAM Investments.
Strategic Partnerships
Together, we address key business challenges, fortifying IAM resiliency. With backup and recovery, we ensure reduced downtime, data integrity, and seamless access. Future-proof your business for 2023 and beyond.
RESOURCE CENTER
From Our Blog
Terraform helps manage Okta as code, but it doesn’t test changes, clone tenants, track identity drift, or recover from...
November 25, 2025
The AWS outage of October 2025 exposed the limits of vendor responsibility. While hyperscalers restore their own infrastructure, IAM...
October 21, 2025
Are You Really IAM‑Audit Ready? 4 Questions to Prove Compliance & Resilience… Auditors are delving deeper, looking beyond basic...
October 10, 2025
Terraform helps manage Okta as code, but it doesn’t test changes, clone tenants, track identity drift, or recover from...
November 25, 2025
The AWS outage of October 2025 exposed the limits of vendor responsibility. While hyperscalers restore their own infrastructure, IAM...
October 21, 2025
Are You Really IAM‑Audit Ready? 4 Questions to Prove Compliance & Resilience… Auditors are delving deeper, looking beyond basic...
October 10, 2025






