Okta MGM Breach: ALPHV Breaks its Silence
On 14th September 2023, News broke the story with an alarming update: the shadowy ransomware group ALPHV had released a detailed statement concerning their attack on MGM Resorts International.
In their disclosure, ALPHV sought to correct the narrative surrounding the breach, shedding light on MGM’s vulnerabilities and offering a candid look into the operational tactics of contemporary cybercriminals.
MGM Hack Exposed via Okta
Central to ALPHV’s account of the breach is the revelation surrounding MGM’s use of Okta, a renowned Identity and Access Management (IAM) platform.
The group detailed their infiltration into MGM’s Okta Agent servers, where they were
"sniffing passwords of people whose passwords couldn't be cracked from their domain controller hash dumps."
This tactic left MGM in a precarious situation, eventually pushing them to make the hasty decision to shut down all their Okta Sync servers.
The outcome?
MGM found themselves completely locked out of their own Okta system.
IAM systems are pivotal for organizations. As the events unfolded at MGM, the vulnerability of their IAM platform became a glaring focal point. With such extensive access, ALPHV boasted,
"we continued having super administrator privileges to their Okta, along with Global Administrator privileges to their Azure tenant."
The Human Factor: MGM’s Critical Missteps
In the realm of cybersecurity, it’s easy to focus solely on the technological components. Yet, as Muli Motola, CEO and co-founder of Acsense, often emphasizes,
"The major risk is the social attack, and you can't be 100% safe when dealing with people."
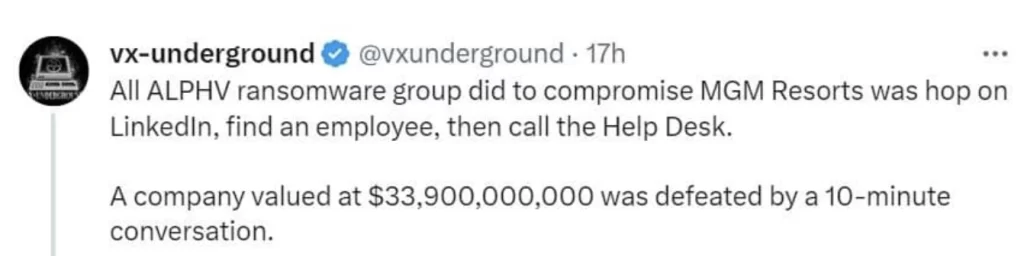
MGM’s actions, as narrated by ALPHV, highlighted the monumental role of the human element. Whether it was the hasty shutdown of crucial servers, the inadequate response playbooks, or their network engineers’ lack of understanding of the network’s functioning, the human decisions made amidst the crisis played into ALPHV’s hands.
Unraveling Infrastructure: The IAM Challenge
ALPHV’s incursion into MGM’s Okta Agent servers wasn’t just a technical breach.
"The attack alters your infrastructure posture," observes Motola.
When the very foundation that controls access and identity becomes compromised, it doesn’t merely pose a technical challenge—it reshapes how the organization operates, how it perceives security, and how it ultimately serves its stakeholders.
The Value of Backup: A Hard Lesson Learned
As the breach evolved, the importance of recovery mechanisms became abundantly clear. ALPHV’s subsequent ransomware attack on over 100 ESXi hypervisors in MGM’s environment post their shutdown underscored the significance of robust backup systems.
Motola’s perspective becomes particularly relevant here,
"The attack alters your infrastructure posture. The only way to recover is through backup."
This incident isn’t unique to MGM; it’s a wake-up call for all businesses. Backup is more than a best practice; it’s essential protection when dealing with cyber criminals, especially for crucial systems like IAM.
The Bigger Picture: ALPHV’s Revelations and the World of Cyber Threats
ALPHV’s statement goes beyond just the MGM breach.
Their disclosure touches upon the challenges of attributing cyberattacks, the dynamics of insider trading, and the pitfalls of hurried and uninformed incident responses. Furthermore, their threats of continued access and potential further attacks on MGM’s infrastructure highlight the evolving and persistent nature of cybersecurity threats in today’s digital age.
Wrapping Up
The public claim of responsibility for the MGM breach by the ALPHV group serves as a significant wake-up call for industries everywhere. In the unpredictable arena of cyber threats, businesses can’t afford to be passive or naive.
Muli Motola’s insights shed light on this reality:
"You can't merely rely on reading an attacker's next move.
Their methods to deceive and manipulate are vast and varied. This reinforces the need to always have a 'golden copy' of data on standby.
Whether it's for a rollback after minor disruptions or, in graver situations where access is wholly compromised, to initiate a complete failover to an alternative disaster recovery infrastructure."
This MGM situation punctuates the message: Ensuring robust backup, especially for critical systems like IAM, isn’t a luxury—it’s a necessity.
Take the Next Steps to Secure Your IAM Infrastructure
Download Our Free Guide:
For a complete, step-by-step guide to crafting your own IAM recovery plan, download our comprehensive guidebook here.

While our guide provides a comprehensive roadmap for IAM resilience, we understand that every organization’s needs are unique.
Schedule a demo with our experts to explore how Acsense’s IAM Resilience Platform can fortify your Okta system against threats and ensure your business continuity.
Don’t leave your IAM resilience to chance.

