The IAM Resilience Platform
Acsense eliminates IAM downtime and compliance gaps through real-time protection, posture intelligence, automated recovery, and configuration management—ensuring operational continuity and resilience.


Protect Your IAM Data
Minimize Downtime
Simplify Compliance

Acsense Architecture
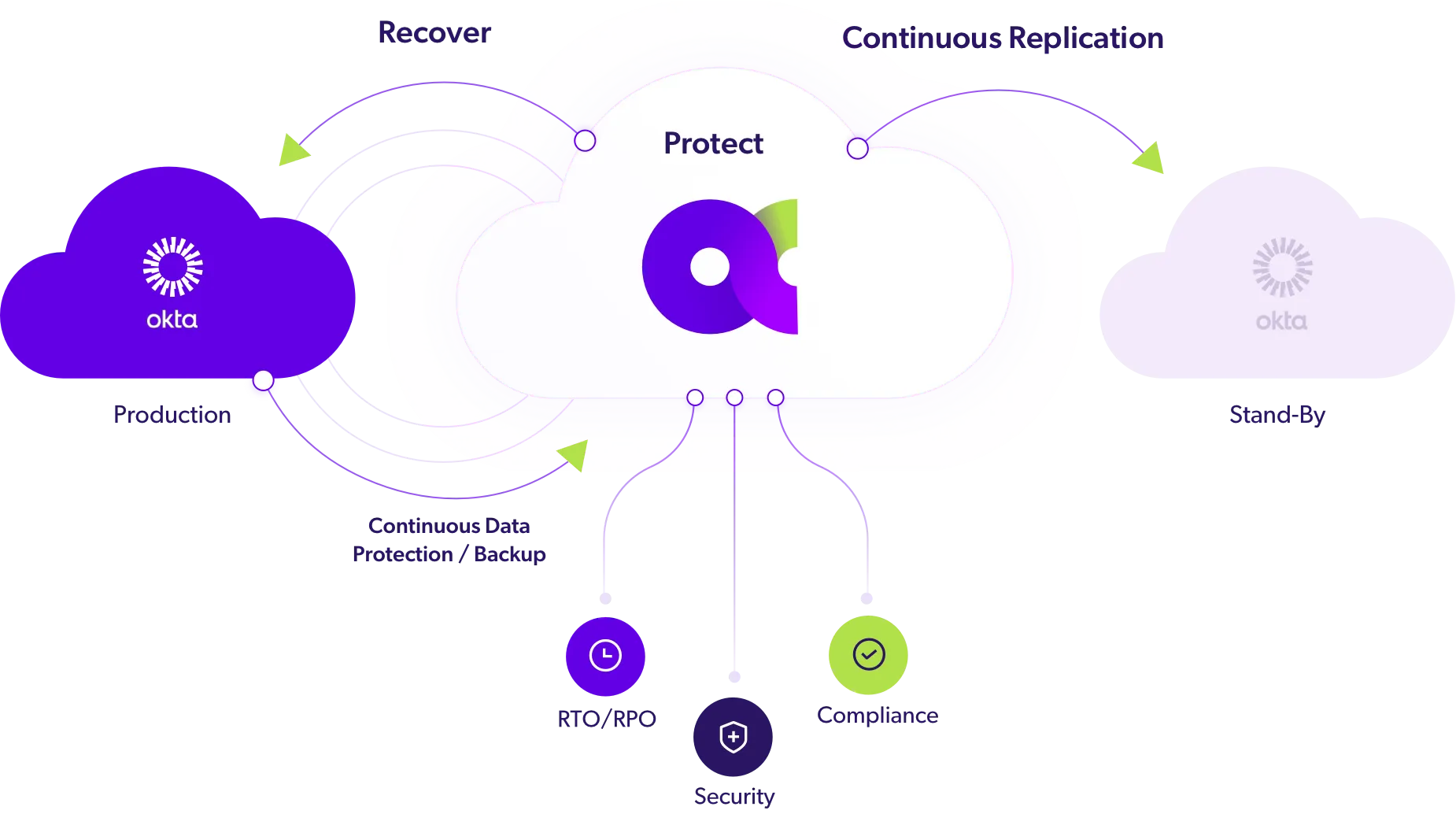
USE CASE/ : DATA PROTECTION
Backup & Recovery
Protect your identity data ensuring you can recover from attacks, outages, or missteps without gaps or delays.
Continuous Data Protection (RPO ~10 mins)
Single Object Recovery (single items)
Full Object Recovery (linked items)
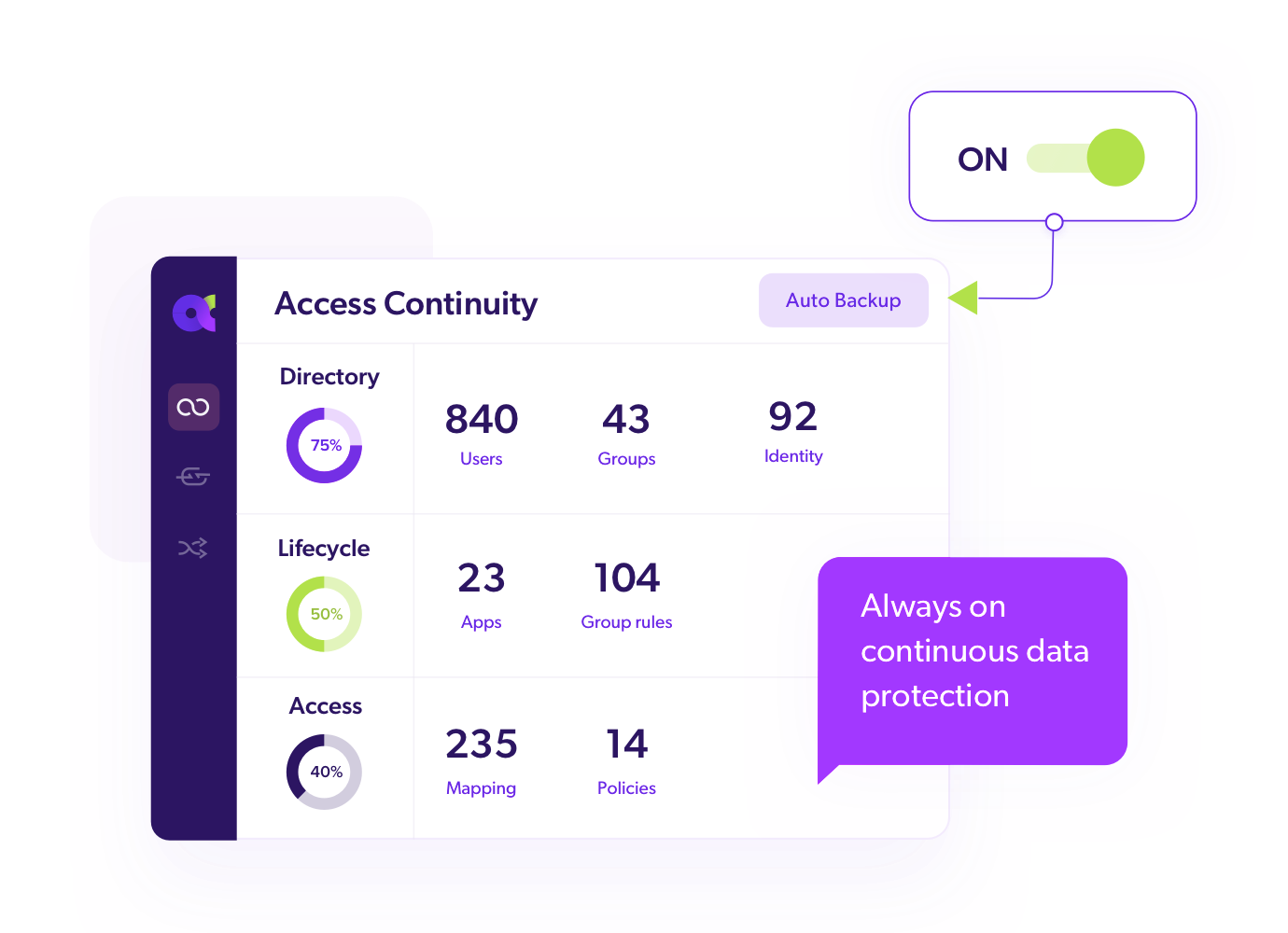
Continuous Data Protection (RPO ~10 mins)
Continuous backups provide near real-time protection, eliminating the need for traditional scheduled daily and weekly backup windows.
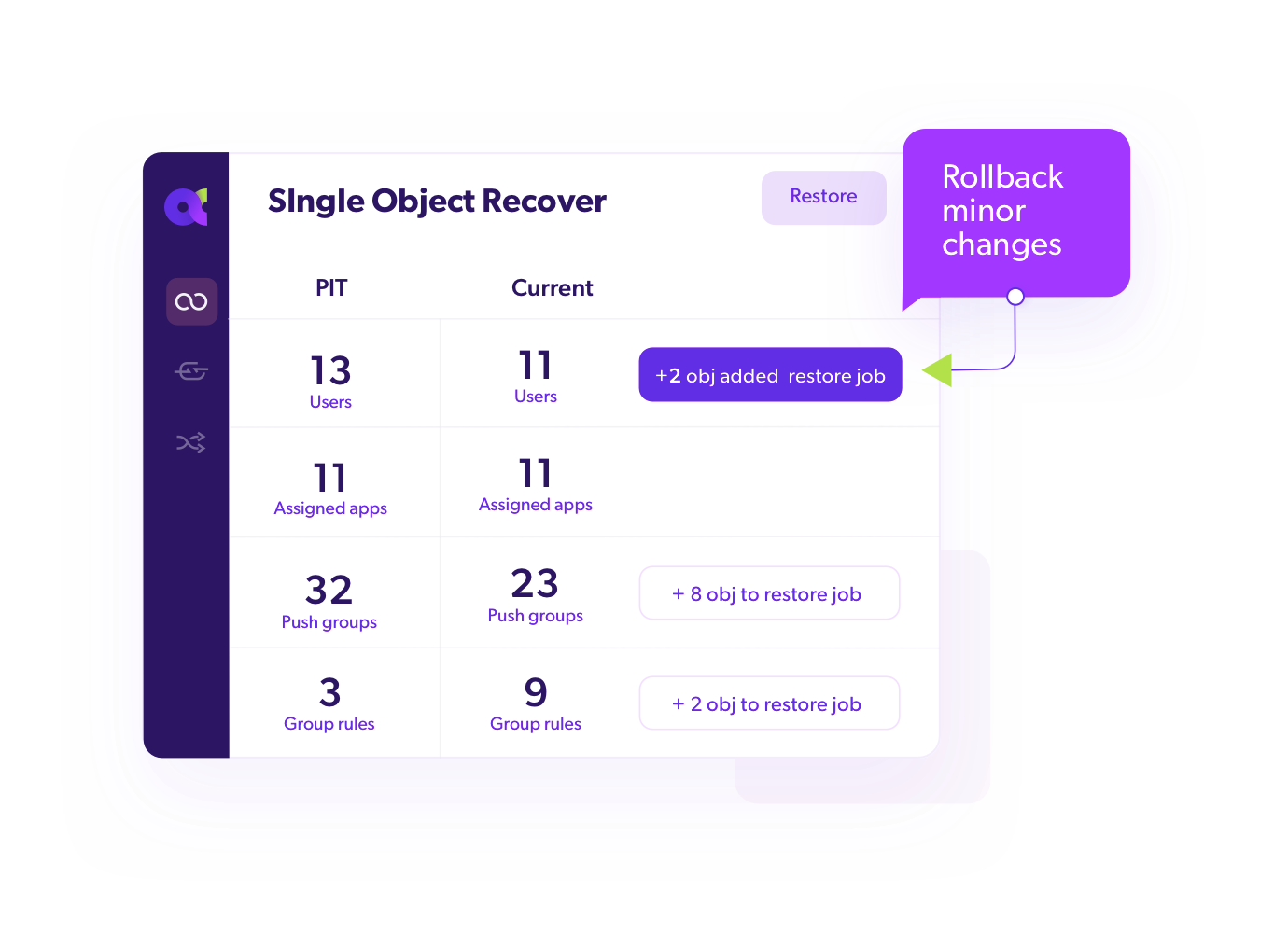
Single Object Recovery (single items)
Rollback single item changes instantly.
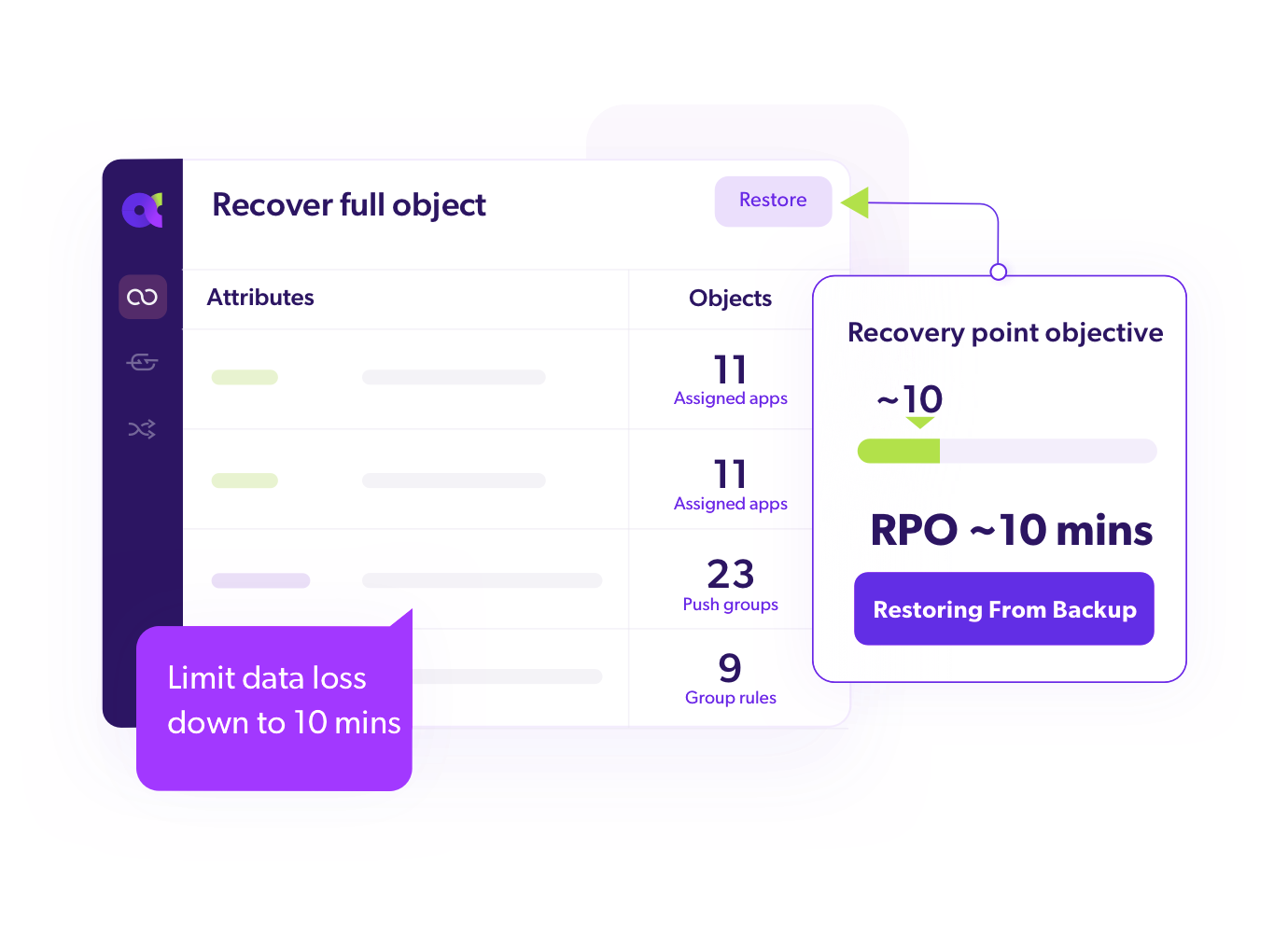
Full Object Recovery (linked items)

Continuous Data Protection (RPO ~10 mins)
Continuous backups provide near real-time protection, eliminating the need for traditional scheduled daily and weekly backup windows.

Single Object Recovery (single items)
Rollback single item changes instantly.

Full Object Recovery (linked items)
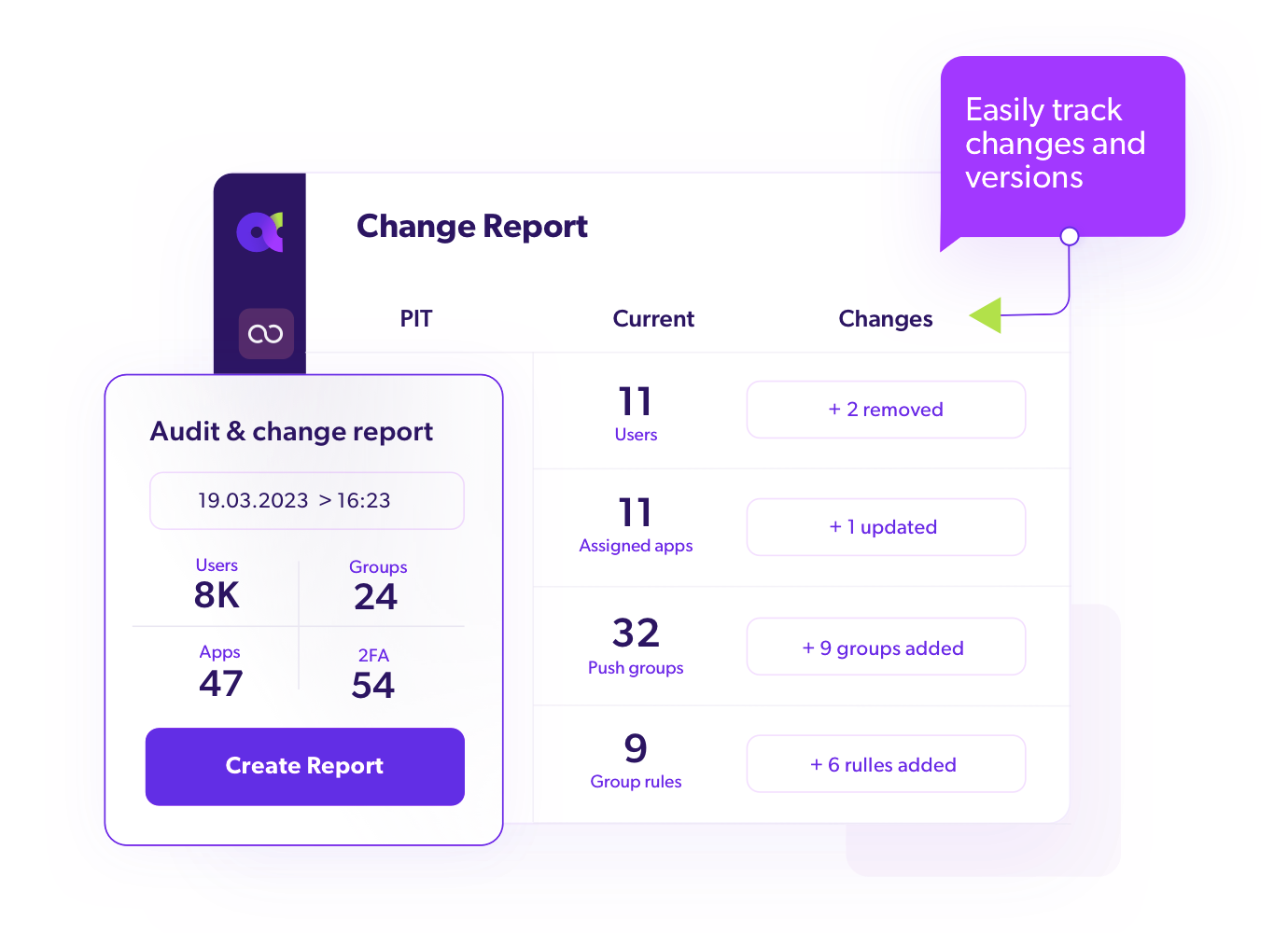
Audit-Ready Versioning
Track and manage changes with ease to meet compliance demands, generating ready-to-use recoverability reports.
Isolated Recovery Environment
In line with the 3-2-1 backup rule, a copy of your data is kept in an isolated “air-gapped” recovery environment, ensuring a reliable recovery.
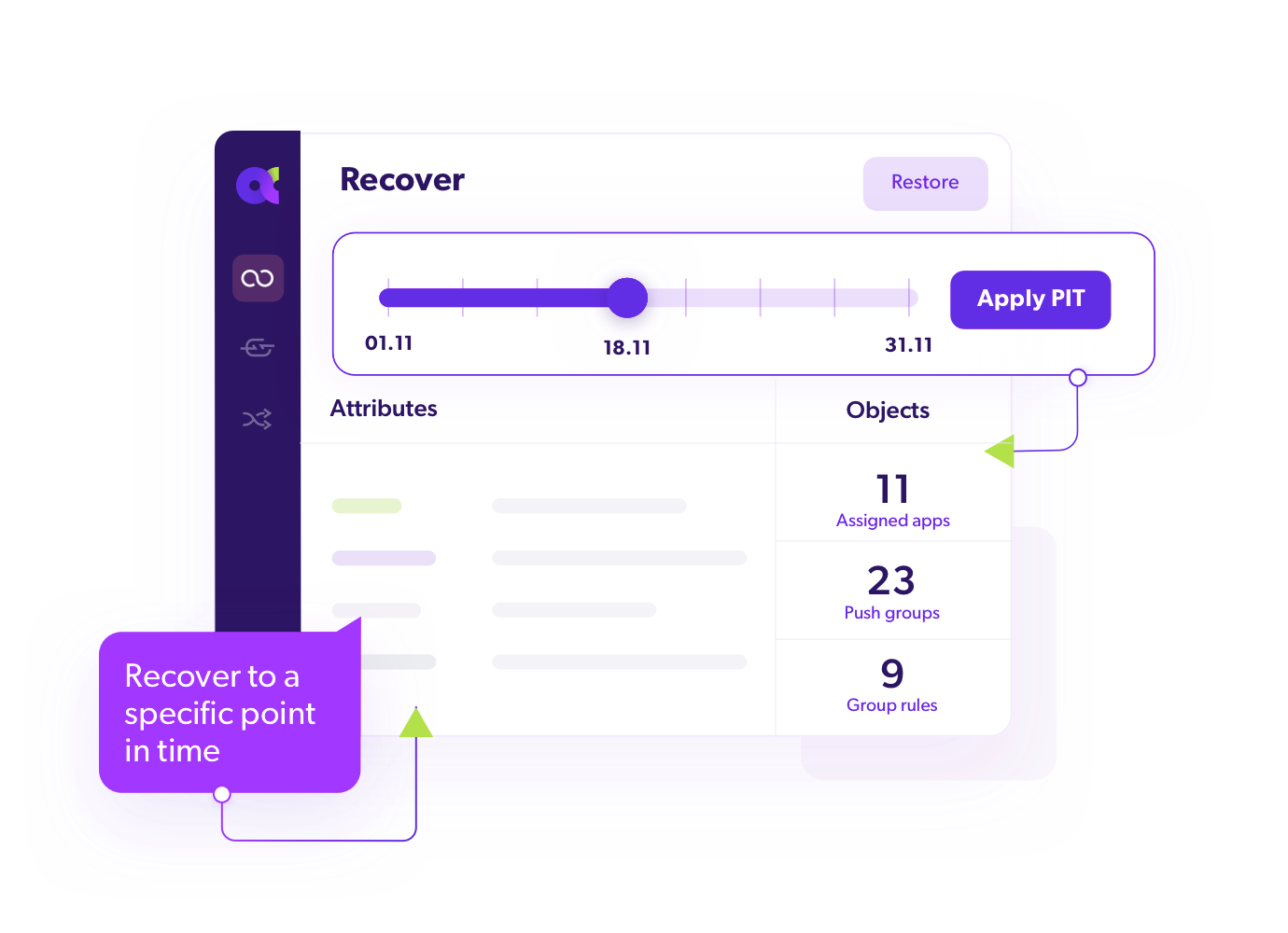
Any Point-in-Time Investigation
Compare system states at different points in time to swiftly investigate incidents, prepare for recovery, locate human errors, or to detect a cyber incident.
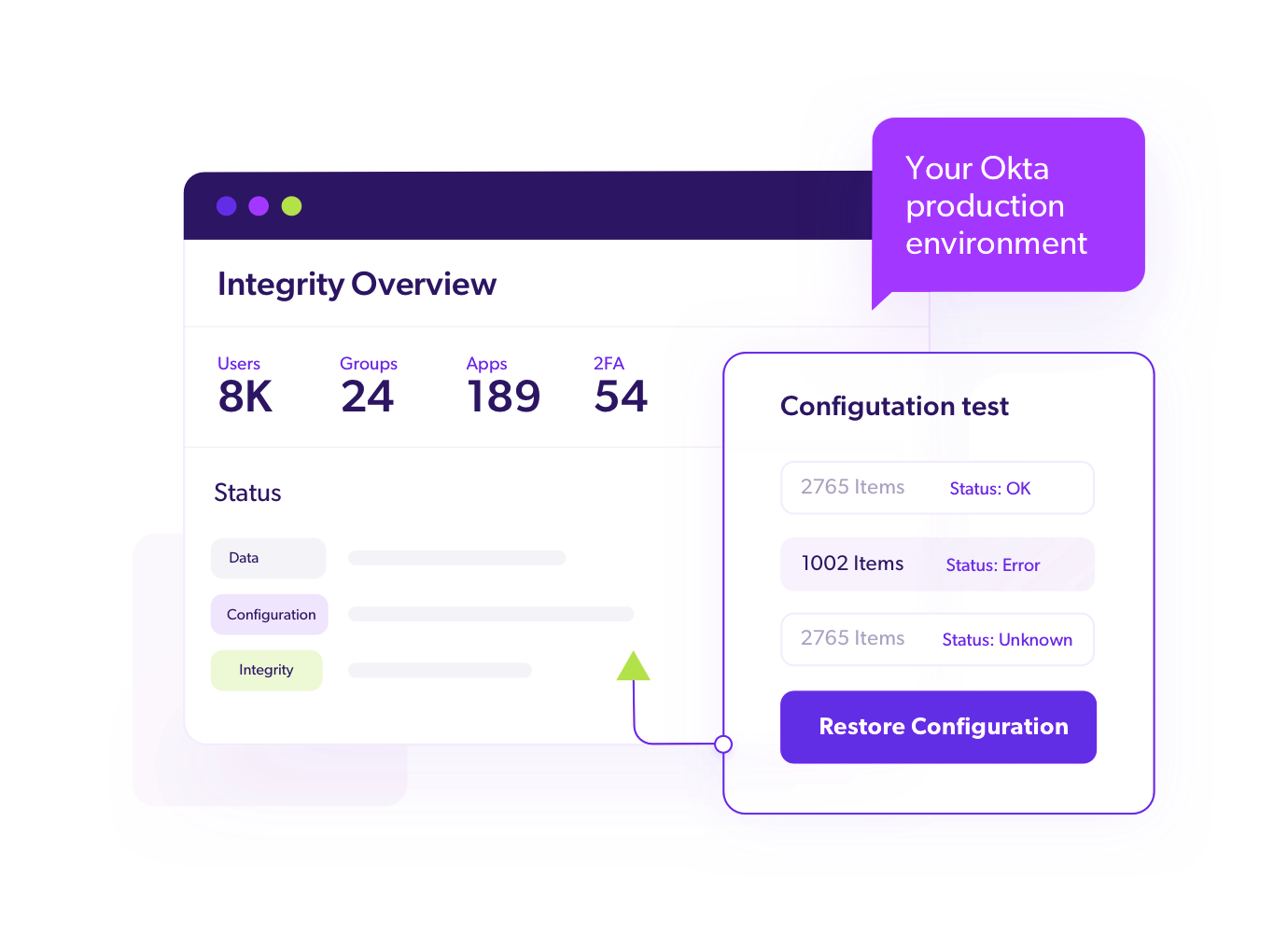
Continuous Integrity Checks
Ensure that your data and configurations can be trusted and used to recover to normal operations.
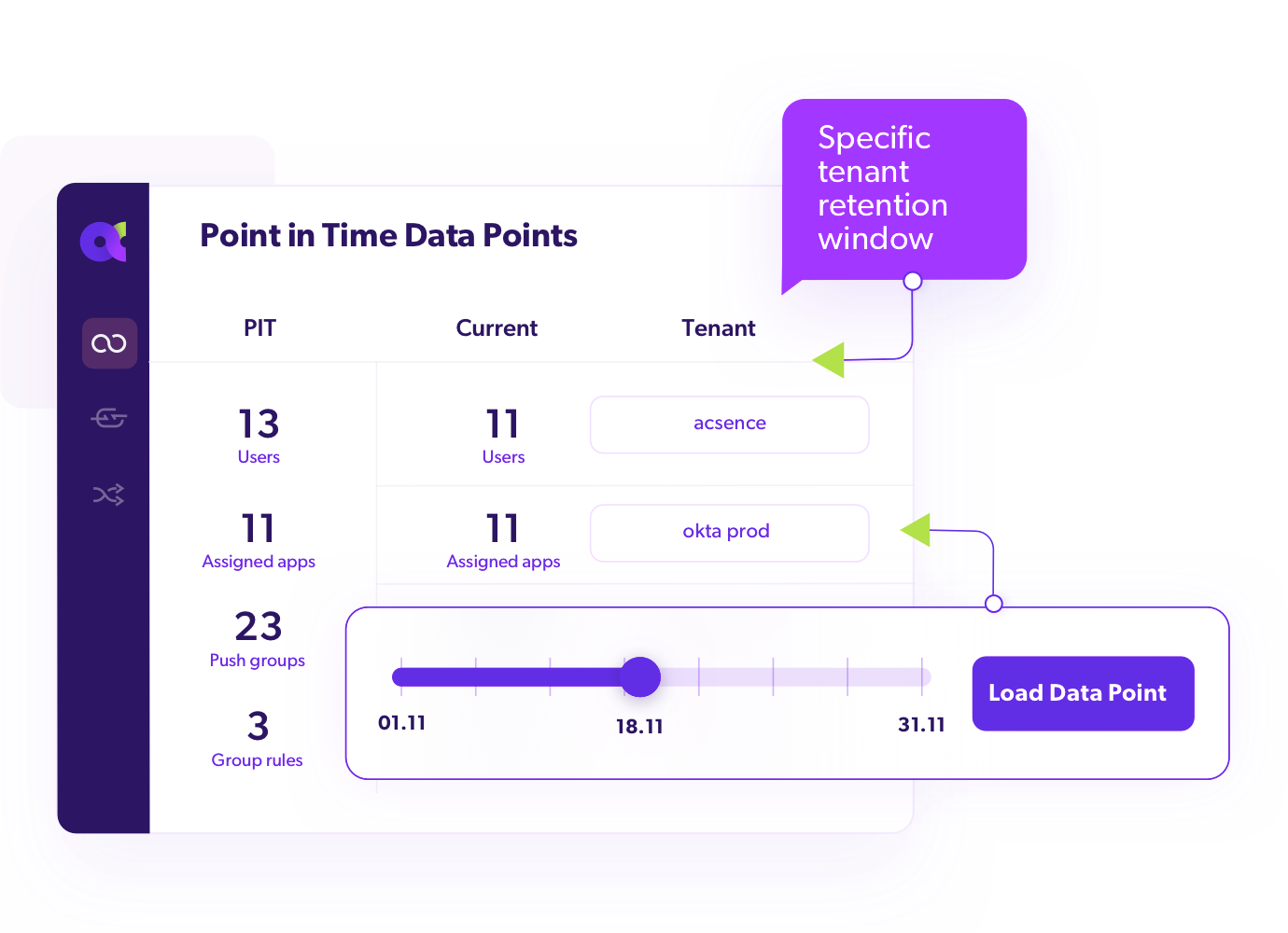
Infinite Retention & Immutable Backups
To address any regulatory requirements, any retention window can be assigned to a specific tenant, and your backup remains secure and unalterable.

Audit-Ready Versioning
Track and manage changes with ease to meet compliance demands, generating ready-to-use recoverability reports.

Isolated Recovery Environment
In line with the 3-2-1 backup rule, a copy of your data is kept in an isolated “air-gapped” recovery environment, ensuring a reliable recovery.

Any Point-in-Time Investigation
Compare system states at different points in time to swiftly investigate incidents, prepare for recovery, locate human errors, or to detect a cyber incident.

Continuous Integrity Checks
Ensure that your data and configurations can be trusted and used to recover to normal operations.

Infinite Retention & Immutable Backups
To address any regulatory requirements, any retention window can be assigned to a specific tenant, and your backup remains secure and unalterable.
USE CASE/ : VISIBILITY & OBSERVABILITY
Incident Investigation
See what changed, who changed it, and how it impacts security posture across essential standards like HIPAA, NIST, SOC2, and ISO 27001.
Change and Audit Trail Reports
Tenant Investigation
Continuous Tracking of Changes
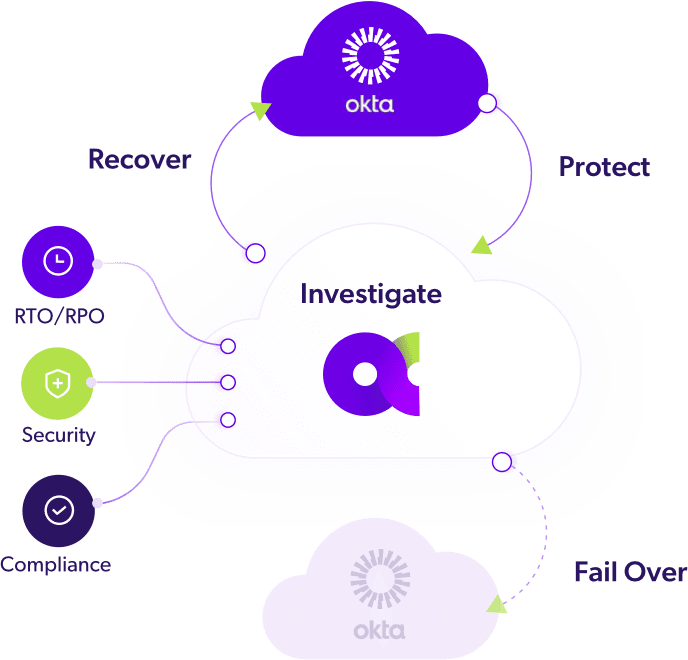
USE CASE/ : DISASTER RECOVERY
Business Continuity/Disaster Recovery (BC/DR)
Bounce back from IAM ransomware in minutes—not days. Eliminate unneeded costs for complex recovery and downtime.
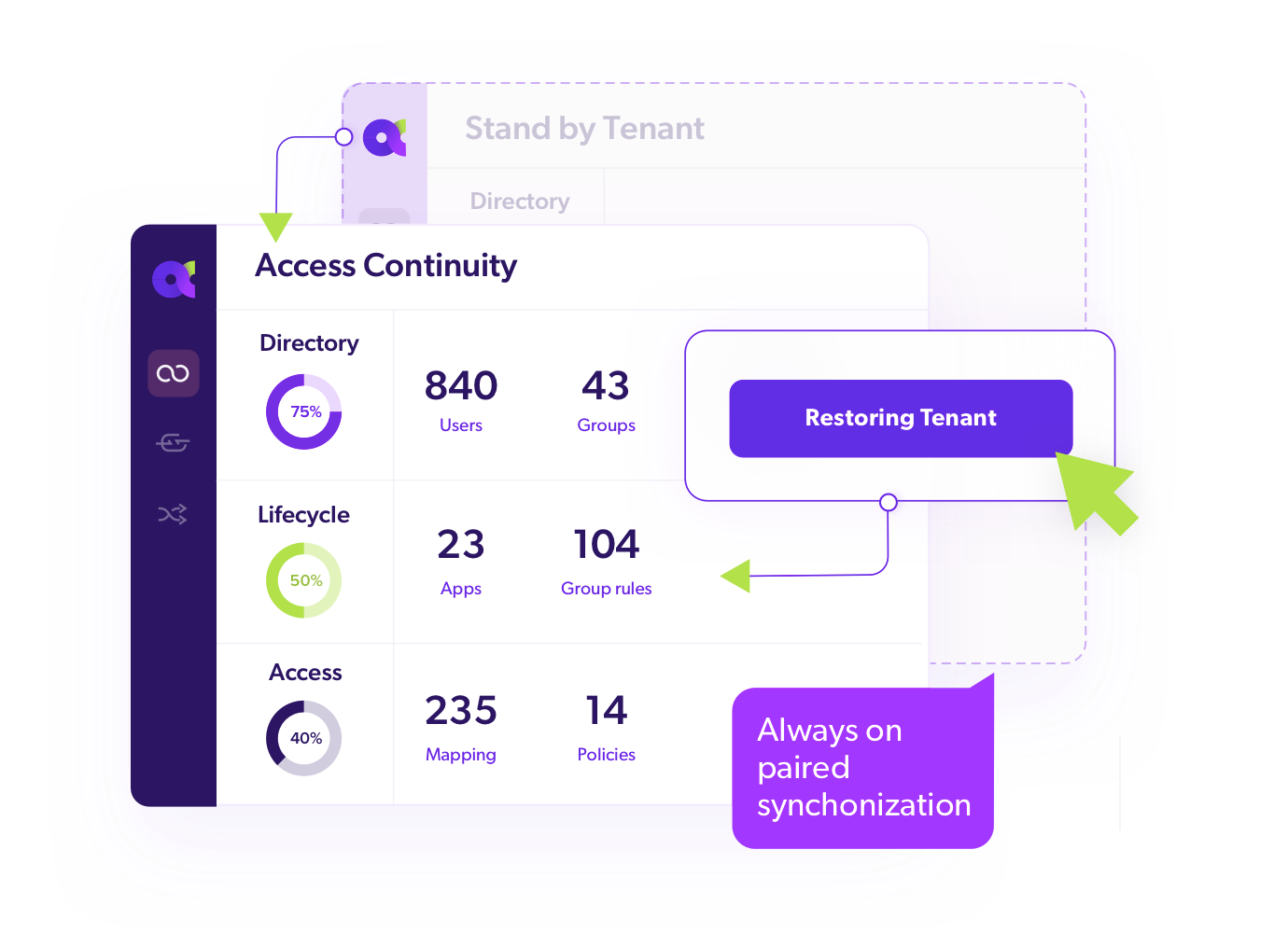
Hot Standby Tenant
Continuous Tenant Replication
Automated Tenant Failover
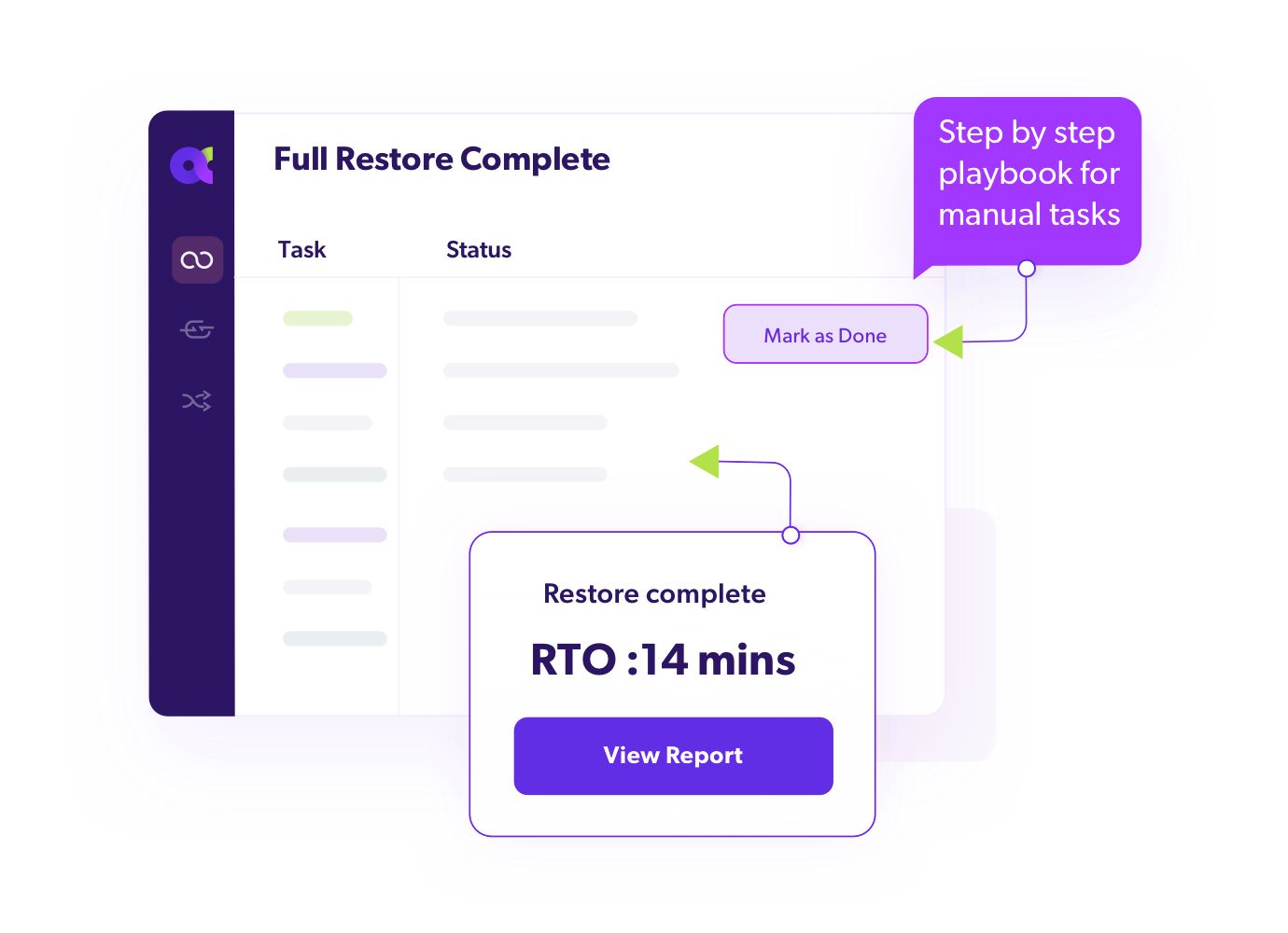
Automated Tenant Failover
Switch to standby IAM tenant instantly during disruptions.

On-Demand Failover
Maintain a failover-ready IAM environment for immediate ransomware recovery
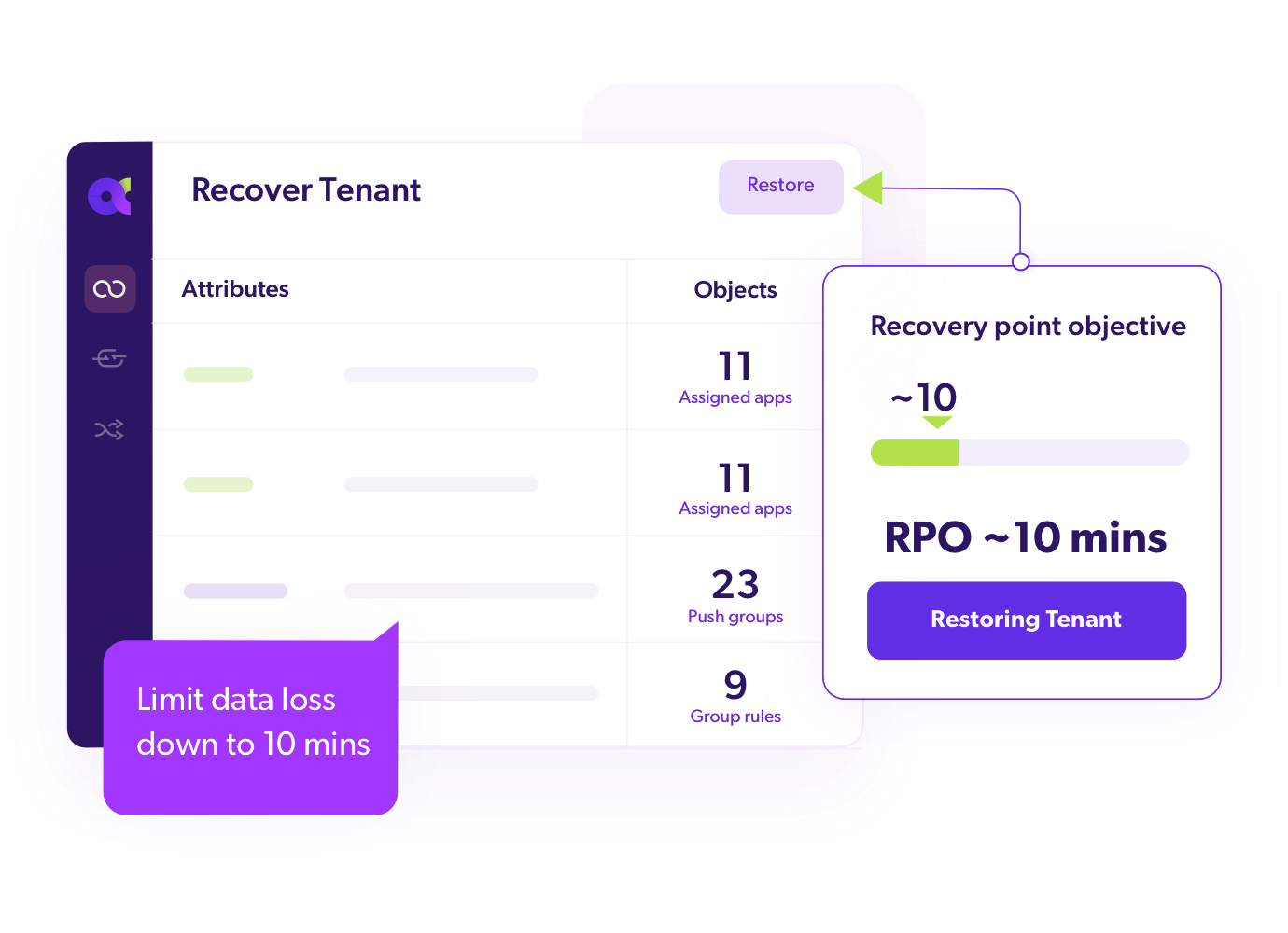
Continuous Replication
Synchronize IAM configurations with ~10 minute RPO to minimize data loss.
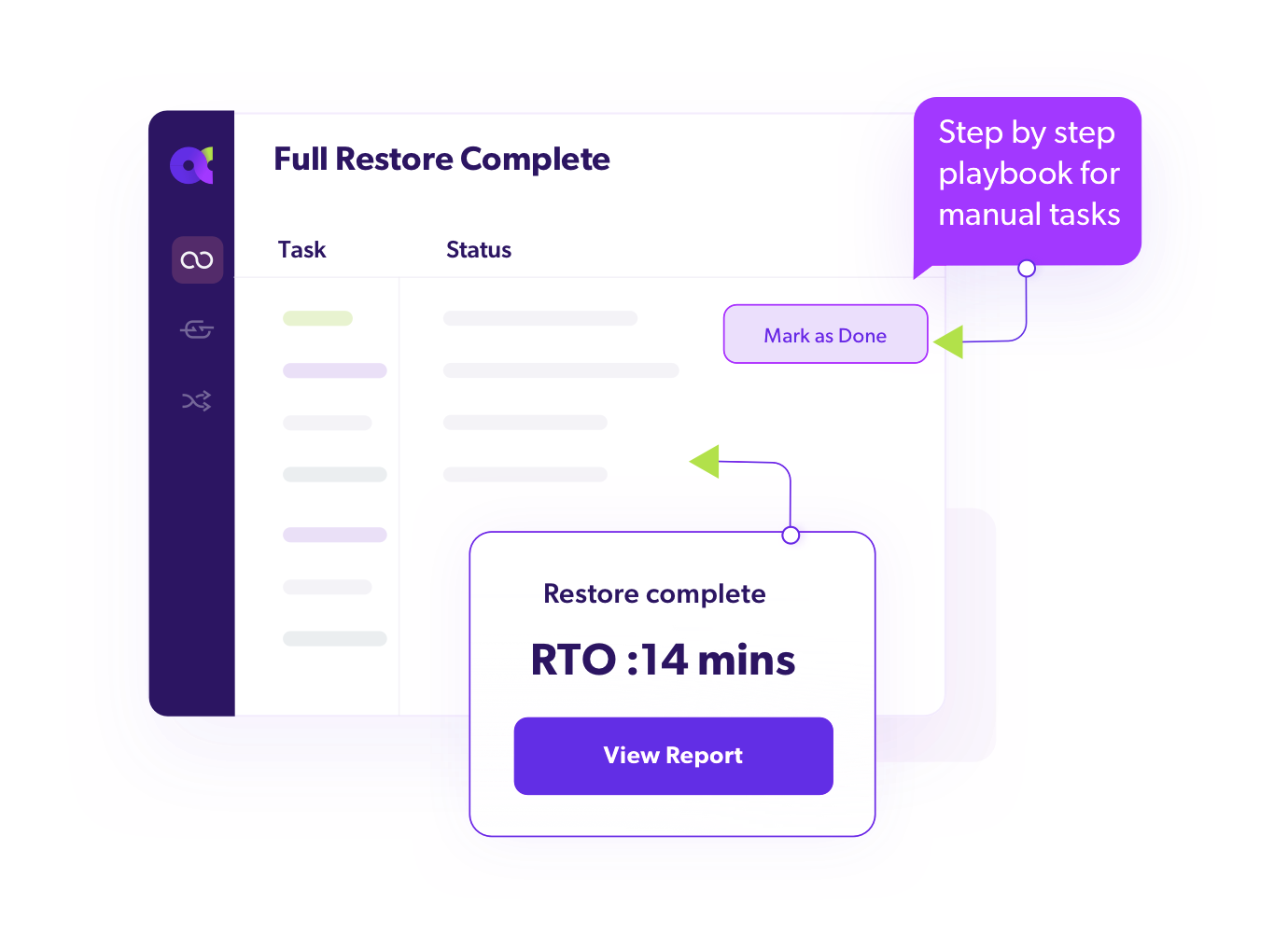
Automated Tenant Failover
Switch to standby IAM tenant instantly during disruptions.

Automated Tenant Failover
Switch to standby IAM tenant instantly during disruptions.

On-Demand Failover
Maintain a failover-ready IAM environment for immediate ransomware recovery

Continuous Replication
Synchronize IAM configurations with ~10 minute RPO to minimize data loss.

Automated Tenant Failover
Switch to standby IAM tenant instantly during disruptions.
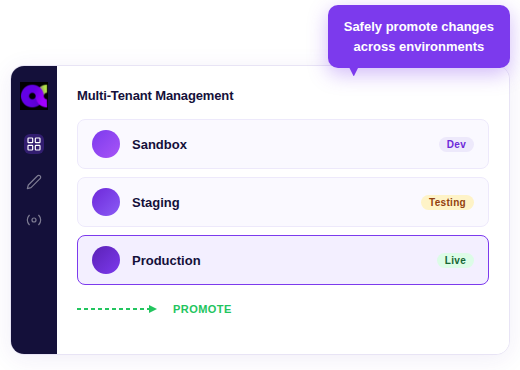
Multi-Tenant Management
Centrally oversee and control all Okta environments from a single interface including Realms.
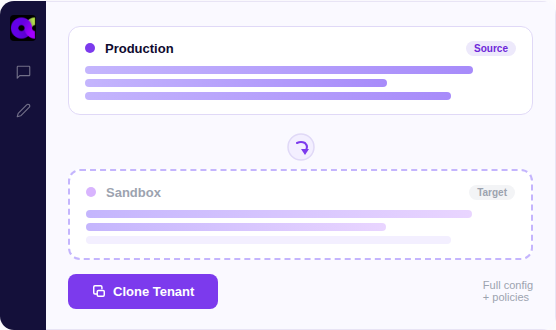
Sandbox Seeding
Instantly replicate production configurations into test environments to ensure reliable change validation and policy testing.
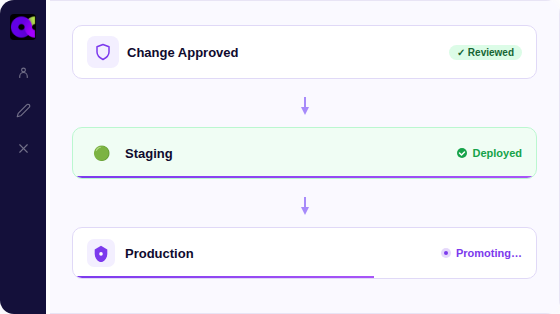
Safe Change Promotion
Promote tested configuration changes across tenants—safely and selectively—with built-in guardrails for IAM resilience.

Multi-Tenant Management
Centrally oversee and control all Okta environments from a single interface including Realms.

Sandbox Seeding
Instantly replicate production configurations into test environments to ensure reliable change validation and policy testing.

Safe Change Promotion
Promote tested configuration changes across tenants—safely and selectively—with built-in guardrails for IAM resilience.
USE CASE/ : OPERATIONS
Configuration Management
Organize your Okta environment for safe,
testable changes— all tracked in one place
Multi-Tenant Management
Full Tenant Replication
Cross Tenant Change Promotion
Is Your Okta Tenant Truly Recoverable?
Explore insights into the recoverability of your Okta tenant with Acsense.
