Okta Disaster Recovery and Its Limitations
In today’s complex cybersecurity landscape, ensuring the resilience of Identity and Access Management (IAM) systems is critical for business continuity. Platforms like Okta are at the heart of enterprise security, enabling organizations to securely manage user identities and access controls.
While Okta provides Enhanced Disaster Recovery (EDR) features to maintain service availability during outages, its capabilities are limited when addressing data-layer threats like ransomware attacks, super admin takeovers, or malicious misconfigurations. These gaps highlight the importance of a comprehensive disaster recovery strategy that extends beyond infrastructure-level availability to include data-layer resilience.
Okta has become a cornerstone of identity management for organizations worldwide. But what happens when disaster strikes? Without a comprehensive Okta disaster recovery plan, businesses risk prolonged downtime, compliance violations, and disrupted operations.
Acsense offers the industry’s leading Okta disaster recovery solution, designed to restore access and business continuity in under 10 minutes. Whether you need fast Okta tenant recovery or an advanced IAM disaster recovery strategy, Acsense simplifies every step.
This blog explores the limitations of Okta’s disaster recovery approach and how Acsense fills critical gaps to deliver unmatched IAM resilience.
The Significance Of Okta Disaster Recovery Planning
As cyber threats and data breaches become increasingly prevalent, organizations must prioritize the effectiveness of their disaster recovery (DR) plans.
A well-crafted disaster recovery strategy acts as the foundation for an organization’s response to unexpected incidents, ensuring minimal disruption and the protection of vital business functions. For Identity and Access Management (IAM) systems like Okta, this involves not only maintaining service availability but also safeguarding the integrity and confidentiality of sensitive user data.
Developing a comprehensive disaster recovery plan for your IAM system entails several critical components:
1. Risk Assessment
The initial step in effective disaster recovery planning involves identifying potential risks that could jeopardize your IAM system. By conducting a meticulous risk assessment, organizations can gain insight into various threats, including natural disasters, cyberattacks, system failures, and human errors. Evaluating these risks enables the development of targeted strategies designed to mitigate specific vulnerabilities and support business continuity.
2. Business Impact Analysis (BIA)
After identifying risks, executing a Business Impact Analysis helps clarify the potential repercussions of various disaster scenarios. This analysis quantifies the effect of downtime on operations, revenue, and user trust, guiding organizations in prioritizing which systems require immediate attention during a disruption. In IAM systems, even minor downtime concerning user data access can yield considerable operational hurdles and reputational damage.
3. Defining Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO)
Establishing precise Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) is crucial for an effective disaster recovery plan. RTO signifies the maximum acceptable duration to restore services post-disaster, whereas RPO specifies the maximum extent of acceptable data loss.
Key Elements Of a Comprehensive Okta Disaster Recovery Plan
1. Assessment and Risk Analysis:
Before executing a disaster recovery plan, organizations must perform a thorough assessment to pinpoint potential threats. Grasping the risks associated with outages, data loss, and security breaches enables organizations to customize their recovery strategies according to specific requirements.
2. Data Backup Protocols:
A fundamental aspect of a disaster recovery plan is to ensure regular data backups that can be restored quickly. Okta provides automated backup options, but it is essential to supplement these with external, third-party solutions to prevent data loss in scenarios like ransomware attacks.
3. Redundancy and Failover Mechanisms:
Incorporating redundancy for essential systems and networks significantly minimizes downtime. Implementing failover mechanisms guarantees that if one system fails, another can immediately take over, ensuring minimal service interruption. For systems dependent on Okta, establishing these redundancies may entail deploying multiple infrastructure instances, such as application servers and databases, across diverse geographic locations. This distribution strategy can avert localized problems from impacting overall service availability, thereby ensuring uninterrupted access to identity and access management functionalities.
4. Regular Testing and Updates:
Ongoing testing and maintenance of the disaster recovery plan are vital for its success.
Organizations should conduct frequent drills to ensure that all team members comprehend their roles and responsibilities during a crisis. These exercises should simulate a range of disaster scenarios to evaluate response times and recovery protocols. Additionally, as Okta and its related services evolve, it is crucial to maintain comprehensive documentation and regularly update recovery procedures, tools, and contact information to align with any infrastructural changes.
Understanding Okta’s Enhanced Disaster Recovery (EDR) Capabilities
Overview of Okta’s DR Capabilities
Okta’s EDR is designed to ensure that its services remain operational during various disruptive events, with features such as:
- Data Redundancy and Replication: Safeguards service availability through multi-region, multi-data center infrastructure.
- Geographic Distribution: Protects against regional failures by distributing data centers across multiple locations.
- Continuous Service Monitoring: Proactively identifies and mitigates issues affecting service availability, such as AWS infrastructure failures or power outages.
Strengths and Limitations
- Strengths:
- Focused on infrastructure resilience to prevent service disruptions during site-wide or regional outages.
- Ensures that Okta’s authentication services remain accessible under most circumstances.
- Limitations:
- Okta’s EDR does not address data-layer threats such as unauthorized configuration changes, data corruption, or ransomware attacks.
- Recovery of customer-specific configurations, user roles, or application integrations requires manual effort, often resulting in prolonged downtime.
Limitations of Okta’s Disaster Recovery
1. Super Admin Takeover Risks
The super admin account in Okta is highly privileged, controlling access to configurations, user policies, and authentication settings.
If compromised, attackers can:
- Lock out legitimate administrators.
- Modify or delete user roles, groups, and application configurations.
- Disable security features such as multi-factor authentication (MFA).
Okta’s EDR focuses on service availability but does not offer mechanisms to recover from malicious changes or a super admin takeover, leaving organizations vulnerable to prolonged disruption.
2. Ransomware in IAM Systems
Attackers increasingly target IAM systems with ransomware tactics, such as:
- Modifying or encrypting critical configurations.
- Deleting user groups or policies.
- Demanding ransom to restore access or prevent further damage.
Okta’s DR measures cannot undo these changes quickly, forcing businesses to rely on time-consuming manual restoration processes.
3. Limited Recovery Time and Point Objectives (RTOs/RPOs)
While Okta ensures rapid recovery of its infrastructure, its capabilities do not extend to granular recovery of customer-specific configurations or user data.
Businesses may face:
- Extended downtime due to manual recovery efforts.
- Potential data loss or misconfigurations that disrupt critical operations.
4. Lack of Granular Data Recovery
Okta’s DR features focus on service continuity rather than restoring specific tenant data, such as deleted user roles or changes to authentication policies.
This limitation poses challenges in recovering from:
- Ransomware
- Insider threats.
- Human errors.
- Misconfigurations during updates or maintenance.
Acsense’s Data-Layer Disaster Recovery (DR) Solution
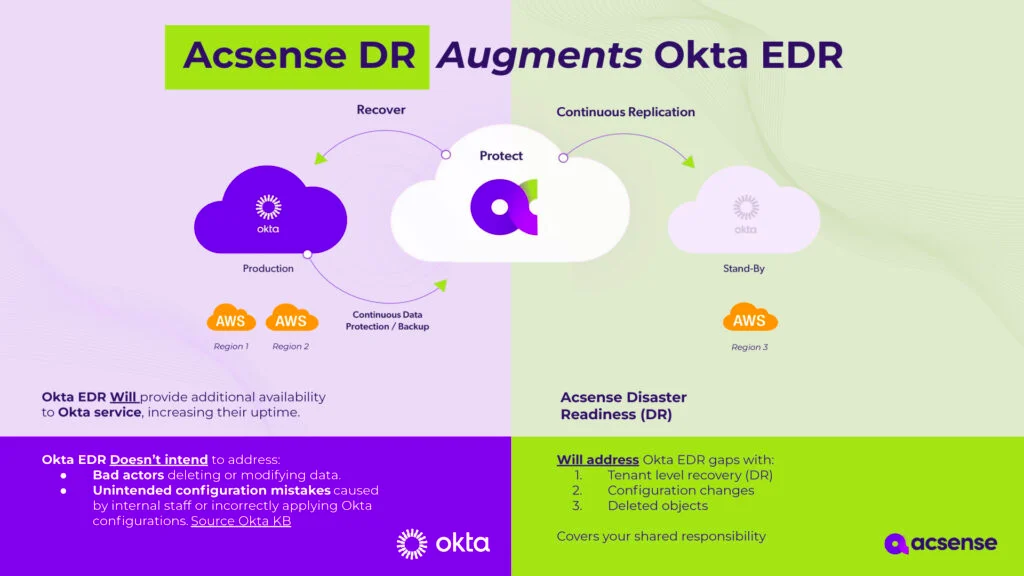
Addressing the Gaps in Okta’s Disaster Recovery
Acsense complements Okta by delivering a data-layer disaster recovery solution that directly addresses gaps in Okta’s EDR capabilities:
- Unauthorized Changes: Protects against super admin takeovers or malicious configuration edits.
- Ransomware Attacks: Ensures rapid recovery of critical configurations without manual intervention.
Acsense’s Comprehensive DR Features
Acsense’s DR capabilities provide organizations with unmatched resilience:
- Point-in-Time Recovery: Roll back to a secure state at any moment to undo malicious or accidental changes.
- Tenant-Level Reversion: Restore an entire Okta tenant, including configurations, user roles, and authentication policies.
- Continuous Backup: Protects all configurations and data with constant backups, ensuring nothing is lost.
- Proactive Change Monitoring: Identifies unauthorized changes to the IAM environment in real time, enabling swift responses.
- Integrity Testing: Regular checks and validations ensure that the backups and configurations are intact and uncorrupted.
Real-World Disaster Recovery Scenarios
Scenario 1: Super Admin Takeover
Attack:
A phishing attack compromises the super admin account, granting attackers unrestricted control. They lock out legitimate admins, delete critical user roles and groups, and disable MFA, rendering the IAM environment unusable.
Okta’s Limitation:
Okta EDR cannot revert these changes. Administrators are forced to manually rebuild the entire tenant from scratch, including user roles, configurations, and security policies—a time-consuming and error-prone process that leaves the organization vulnerable to prolonged downtime.
How Acsense Helps:
- Immediate Recovery: Roll back tenant configurations to a secure state before the attack.
- Access Restoration: Rapidly reestablish MFA and user roles in minutes, minimizing downtime.
- Standby Tenant Advantage: Acsense maintains a hot standby tenant, enabling seamless failover to restore operations quickly and efficiently.
Scenario 2: Ransomware Attack
Attack:
A ransomware attack targets your IAM system, encrypting or deleting critical authentication policies and tenant configurations. This renders applications inaccessible and disrupts business operations, forcing organizations to start from scratch.
Okta’s Limitation:
While Okta’s infrastructure remains operational, it does not provide a mechanism to recover encrypted or deleted configurations automatically. Organizations must manually rebuild the entire tenant, including authentication policies and application integrations, resulting in significant downtime and operational costs.
How Acsense Helps:
- Rapid Restoration: Recover deleted authentication policies and configurations with one-click recovery.
- Continuous Protection: Backups ensure no critical configurations are permanently lost.
- Standby Tenant Advantage: Failover to the hot standby tenant ensures swift recovery and
Compliance and Regulatory Considerations
Regulatory frameworks like GDPR, HIPAA, and ISO 27001 require organizations to maintain robust disaster recovery capabilities, including the ability to prove a failover to ensure business continuity, data integrity, and availability.
Okta’s EDR Compliance Gaps:
- Limited ability to prove failover or recoverability of configurations and data.
- No mechanisms for detailed, on-demand compliance reporting.
Acsense’s Compliance Advantage:
- Continuous Integrity Checks: Validate the recoverability of all configurations, data, and failover processes.
- Standby Tenant for Proven Failover: Acsense’s hot standby tenant provides demonstrable failover capabilities, ensuring regulatory compliance and uninterrupted operations.
- On-Demand Compliance Reporting: Simplify audits with instant, detailed reporting of recovery readiness, ensuring confidence in meeting regulatory requirements.
Building a Resilient IAM Strategy
Organizations can overcome Okta’s disaster recovery limitations by:
- Implementing Acsense for Data-Layer Resilience: Complement Okta’s EDR with Acsense’s tenant-level recovery, point-in-time rollback, and real-time monitoring.
- Regular Testing of DR Scenarios: Simulate potential disaster scenarios to ensure readiness.
- Adopting IAM Resilience Best Practices: Proactively secure privileged accounts and ensure rapid recovery options are in place.
Conclusion
While Okta’s disaster recovery ensures service availability during infrastructure disruptions, it falls short in addressing critical data-layer risks such as ransomware, insider threats, and super admin takeovers. Acsense bridges these gaps with a comprehensive disaster recovery solution designed to protect IAM systems at every layer.
Don’t leave your IAM environment vulnerable—explore how Acsense can transform your disaster recovery strategy. Schedule a Demo with Acsense
The Ultimate Guide to Crafting an Okta Disaster Recovery Plan on Any Budget.
If you’d like to delve further into the topic, our comprehensive white paper offers an in-depth look at the subject of disaster recovery for Okta.
FAQs About Okta Disaster Recovery
Q: What makes Acsense different from backup solutions?
A: Acsense is a complete Okta disaster recovery solution, automating recovery processes, preserving configurations, and minimizing downtime. Traditional backups only store data without addressing recovery complexity.
Q: How fast can Acsense recover my Okta tenant?
A: Acsense’s one-click recovery restores your tenant—including SAML apps and configurations—in under 10 minutes.
Q: Does Acsense support compliance requirements?
A: Yes, Acsense simplifies compliance with on-demand reports and automated recovery testing that meets SOC2 and ISO 27001 standards.