The Importance of Okta Data Backup and Recovery
The importance of Okta data backup and recovery cannot be understated. As an IAM solution, Okta holds crucial information such as user identities, access privileges, and application configurations. Losing this data can have severe consequences for your organization, including security breaches, loss of productivity, and regulatory non-compliance.
“Most organizations think they are protected once everything is on the cloud.
That if a cyber, ransomware, malware attack, or even a misconfiguration will happen, you will have the ability from your SaaS provider to recover.
This is simply not true… You can only trust yourself and your organization.”
— Lior Zagury, Director of Global IT
Monday.com
The Unseen Risks of Neglecting Okta Backup and Restore
1. Ransomware Attack
Ransomware attacks have become increasingly prevalent in recent years, targeting organizations of all sizes and industries. These attacks involve hackers encrypting an organization’s data and demanding a ransom payment in return for the decryption key. If your Okta data is not properly backed up and the necessary recovery processes are not in place, your organization may find itself at the mercy of these attackers.
2. Human Errors
Human errors are a significant risk when it comes to Okta data management. Accidental deletion, misconfiguration, or unintentional changes to Okta settings can lead to data loss or disruptions in access for your users. Without a reliable backup and recovery solution in place, correcting these human errors can be time-consuming and costly.
3. Compliance
Compliance is a crucial aspect of data management for any organization. Many industries have specific regulations and standards that govern how data should be handled, stored, and protected. Failure to comply with these regulations can result in legal consequences, fines, and damage to your organization’s reputation.
4. Business Continuity
Business continuity is a key concern for organizations. In the event of a system failure, natural disaster, or any unforeseen event, having a solid backup and recovery plan in place ensures that you can quickly restore your Okta data and get your business operations up and running again.
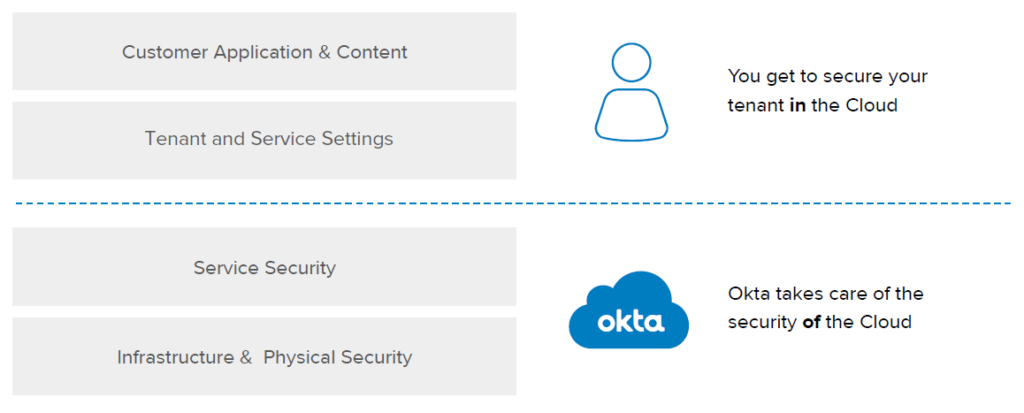
The Shared Responsibility Model Explained
In essence, Okta is accountable for the security of the cloud, while the user is responsible for security within the cloud.
“Our customers are responsible for securing what they host “in” Okta.
This includes, for example, granting the correct permissions to your users, disabling accounts when employees are terminated, enforcing multi-factor authentication, properly configuring and monitoring the authentication policies required to protect your data, reviewing activity data in the system log to ensure users are following your policies, and monitoring your Okta tenants for attacks, such as password spraying, phishing, etc.”
Can You Backup Okta Data & Configurations?
The Short answer is no.Okta does not offer its own backup and recovery solutions.
It’s crucial to distinguish between Okta’s different offerings. While Okta has a backup functionality for its Access Gateway, it doesn’t extend this feature to its core IAM services, thereby necessitating an external solution for backing up Okta configurations and data.
Backup Okta Data & Configurations and Ensure Rapid Recovery with Acsense
To address these critical concerns, Acsense offers an Enterprise IAM Resilience Platform.
Our platform provides continuous backups, quick recovery solutions, and data protection to reduce downtime and costs, fortify IAM security, and enhance overall resilience with:
- Effortless Data Security: Continuous backups and granular, any point-in-time recovery ensure the security of your Okta data and configurations.
- Seamless Continuity: Swiftly recover from IAM disruptions with optimal Return Point Objectives (RPO) and Return Time Objectives (RTO).
- Compliance Mapping: Automated recoverability reports and 3-2-1 aligned infrastructure streamline IAM compliance across standards like SOC2, and ISO 27001.
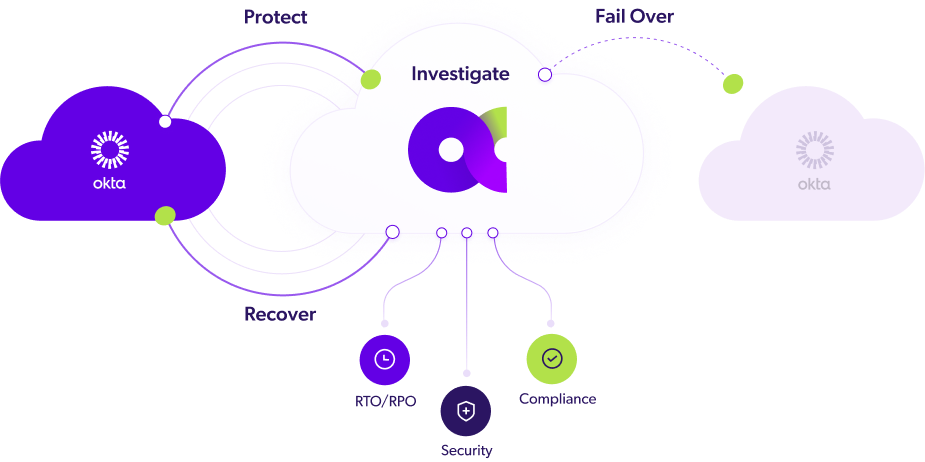
Moreover, our solution architecture encompasses core capabilities and features like:
- Always-On Continuous Data Protection: No more daily, weekly, or incremental backups. Full backups ensure your data is always up to date.
- Any-Point-In-Time (PiT): Go back in time in 10-minute intervals for restoration or investigation purposes.
- Granular or Full Recovery: Available for tenants or specific objects, from any point in time.
- Data Integrity and Verification: Constant recovery tests with reports to address IT compliance and BCP/DRP readiness.
- Air-Gapped and Immutable Backups: Align with Zero Trust and data protection standards.
What Components of Your Okta Data Can Acsense Back Up?
Below are some of the critical Okta components that can be backed up using Acsense:
Access Policies
Access policies are foundational to your IAM security and compliance posture.
Acsense ensures these policies are backed up so you can easily revert to previous settings if they are inadvertently modified or deleted.
User Identities
Your user profiles, including authentication credentials like usernames, emails, roles, and other attributes, are securely backed up. This ensures uninterrupted access to various applications and services even in the case of accidental deletions or modifications.
Groups and Roles
Acsense backs up the groups and roles you’ve configured in Okta, thereby safeguarding your organizational structure and access control mechanisms.
Application Configurations
Your Okta environment likely integrates with a myriad of applications for Single Sign-On (SSO) and user provisioning. Acsense ensures that the configurations and settings for these applications are backed up, facilitating a seamless user experience and reducing IAM downtime.
By leveraging Acsense’s IAM Resilience Platform, your organization benefits from automated backups, one-click recovery, Point-in-Time investigation and restoration, and continuous data verification. These features are all designed to minimize the impact of IAM downtime and reduce associated costs, thereby enhancing your IAM resilience.
For a more comprehensive list and deep dive into all the entity types and how Acsense can back up and protect your Okta data, feel free to schedule a consultation with our team.
Git vs Secured Third-Party Storage for Okta Backups
In an era where cybersecurity threats are escalating, the decision of where to store Identity and Access Management (IAM) backups has become crucial for organizational security. High-profile security breaches, such as the Git RepoJacking incident in June 2023 and the OKTA Git Breach in January 2023, underscore the vital importance of data security.
The question at hand is: Should you store your IAM backups on your Git repository or in a third-party secured storage? To help you make an informed decision, we’ve thoroughly analyzed the pros and cons of each storage option.
For detailed insights, feel free to read our dedicated blog post on The Pros and Cons of Git vs Secured Third-Party Storage for IAM Backups.
Can You Use Terraform to Backup and Recover an Okta Tenant?
This is a common question from teams who rely on Terraform to deploy and configure critical infrastructure.
The Terraform Okta provider is an incredible tool for incorporating identity components into your DevOps pipeline. However, Okta will have data, configuration, and state that will change outside Terraform’s purview, making it impractical for managing highly dynamic data elements.
In short, Okta disaster recovery is not an appropriate use case for Terraform.
A purpose-built tool for Okta disaster recovery will save you time, money, and frustration.
When to Use the Terraform Okta Provider
Terraform can still be effectively used to manage specific IAM configurations in your development pipeline.
For example, custom scopes and claims for a self-hosted modern web application can be configured via Terraform, streamlining the development and deployment process. Terraform can manage client applications, set up scopes, and even place client credentials into a secrets vault, speeding up the development and deployment process.
What Does a Good Okta Backup & Recovery Solution Look Like?
An Okta tenant can generate a lot of data.
Effective backup and recovery involve not just capturing this data but also being able to query backups to a specific point in time. It’s important to maintain the relationships between all the objects in the backup during recovery.
Building this kind of resilience yourself can consume significant time and resources.
Crafting a Comprehensive Okta Backup & Recovery Plan
Planning for disaster recovery is essential.
Our comprehensive white paper, “The Ultimate Guide to Crafting an Okta Disaster Recovery Plan on any Budget,” offers an in-depth look at disaster recovery for Okta.



