Change management for Okta is safer with Acsense.
Capture every update in seconds, route approvals through ServiceNow or Jira, and roll back instantly—no Git repos, pipelines, or secrets required.
TL;DR
Okta admins face constant change risk: one misconfiguration can cause outages, security gaps, and compliance failures. Acsense Configuration Management solves this with a Git-free, ITSM-native workflow. Test in sandbox, promote across tenants, and roll back instantly. Audit-ready reports and hot-standby DR deliver both resilience and speed.
Table of Contents
- Introduction: Why Change Management Matters
- The Problem With Git-Centric IAM Change Management
- The Cost of Mismanaged IAM Change
- Acsense’s Git-Free Approach To Okta Change Management
- How It Works: Step-by-Step
- Detect
- Backup
- Ticket Sync
- Promote
- Rollback
- Prove
- Compliance And Audit Readiness
- Industry-Specific Use Cases
- Real-World Story: From Outage To Confidence
- Business Impact: Why Teams Choose Acsense
- Acsense Vs. Git-Centric Alternatives
- Future Outlook: Why IAM Change Resilience Matters
- Getting Started With Acsense
- Conclusion: Secure Every Okta Change
- FAQ
Introduction: Why Change Management Matters
Identity and Access Management (IAM) platforms like Okta are the backbone of digital enterprises.
Every new application, group update, or MFA policy affects business-critical access. A single misstep can lock out users, stall operations, or expose sensitive data.
Yet, most IAM teams still rely on Git pipelines or manual exports to track and manage changes. These approaches were built for developers writing code — not identity admins maintaining live authentication systems. The result: outages, compliance gaps, and wasted time.
What’s needed is a purpose-built approach to IAM change management — one that ensures every change is safe, reversible, and auditable.
The Problem With Git-Centric IAM Change Management
Git pipelines assume order and predictability. But IAM changes are dynamic, urgent, and high-risk.
Why Git fails for IAM change:
- Outage risk – Mis-scoped policies can immediately break access.
- Secrets exposure – The GitGuardian 2024 Secrets Leak Report found a 43% increase in leaked API tokens, underscoring how fragile repo-based workflows are (GitGuardian).
- Rollback delays – git revert && deploy sounds simple, but in IAM, dependencies (users, groups, policies, apps) make true rollbacks painful.
- Audit gaps – Auditors want proof of control, not just code commits.
As Gartner warns, “By 2026, organizations that prioritize their security investments based on a Continuous Threat Exposure Management (CTEM) program will be three times less likely to suffer a breach.”
Git is powerful for software development, but dangerously mismatched for Okta change management.
The Cost of Mismanaged IAM Change
Mismanaged IAM changes don’t just frustrate admins — they impact the entire business.
- Downtime costs – IBM’s Cost of a Data Breach 2024 Report estimates enterprise downtime costs at $9,000 per minute (IBM). In industries like finance, where trading depends on real-time access, minutes can equal millions.
- Compliance fines – HIPAA violations can cost up to $1.5M per incident, while PCI DSS non-compliance fines range from $5,000–$100,000 per month.
- Audit failures – When rollbacks aren’t provable, SOX and ISO 27001 audits can stall deals and force remediation.
- Reputation damage – For healthcare providers, downtime doesn’t just cost money; it delays patient care and erodes trust.
One misconfigured policy can trigger hours of downtime, regulatory investigations, and lasting customer churn.
Acsense’s Git-Free Approach To Okta Change Management
Acsense delivers Configuration Management for Okta without Git — a solution built for IAM teams.
- Capture First
Detects Okta configuration changes in ~60 seconds and serializes them to immutable, encrypted storage for evidence and recovery. (Aligned with NIST SP 800-218 secure practices.) NIST Publications - ITSM-Native Approvals
ServiceNow/Jira approvals are bound to backup entries for auditability. - Promotion Without Pipelines
Promote only approved changes from sandbox → prod.
No Git, no YAML, no repo secrets to protect—especially relevant given the ongoing rise in exposed secrets. GitGuardian Blog - One-Click Rollback & DR
Restore an object or entire tenant to a specific point in time; hot-standby option helps hit aggressive recovery objectives (consistent with NIST SP 800-53 recoverability goals). NIST Publications - On-Demand Evidence
Generate period-bound reports for SOX, HIPAA/PCI, NIS2/DORA reviews.
Having proven rollback plus bound approvals shortens audits and reduces risk.
Business Impact
IBM’s 2024 study puts the average global breach cost at USD 4.88M, underscoring why recovery speed and strong controls matter. While not every incident is a data breach, the cost baseline reinforces the ROI of rapid, reliable rollback and audit-ready change control. IBM’s cost-of-a-data-breach report
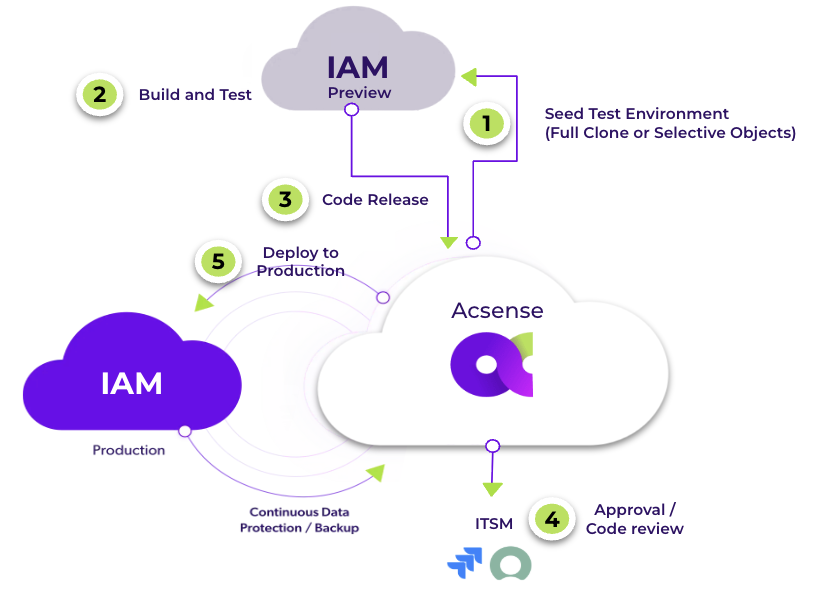
How It Works: Step-by-Step
Seed Test Environment – Create a preview tenant from production (full clone or selective objects) so changes are validated against real-world posture.
Build and Test – Safely test new apps, policies, and group mappings in preview. Acsense continuously backs up configuration changes as you go.
Code Release – Bundle validated changes for promotion; Acsense records the configuration state in the immutable backup history.
Approval / Code Review (ITSM) – Route through ServiceNow or Jira. Approval metadata is bound to the backup history entry for that change, enforcing CAB and segregation of duties.
Deploy to Production – Promote only approved configurations. If something goes wrong, perform a point-in-time restore from the backup history—object-level or full-tenant.
Compliance And Audit Readiness
Auditors expect: evidence, segregation of duties, and repeatability. Acsense delivers all three.
Regulation / Standard | Requirement | How Acsense Helps |
SOX 404 | Trace admin-role changes to tickets | Auto-binds changes to ITSM approvals |
HIPAA | Maintain tamper-proof audit logs | Immutable captures + instant rollback |
PCI DSS | Prove control effectiveness | Exportable recoverability reports |
NIS2 (EU) | Operational resilience + DR | Continuous recoverability health checks |
ISO 27001 | Demonstrate secure change management | Immutable history + versioned config |
DORA (EU Financial Services) | Periodic resilience testing | Automated nightly recoverability tests |
NIST SP 800-53 | Continuous monitoring | Real-time capture + rollback validation |
APRA CPS 230 (Australia) | Operational resilience for financial services | Multi-tenant DR and rollback readiness |
FedRAMP | Audit-ready logs | Immutable, exportable evidence |
Key point: Acsense doesn’t just satisfy audits — it simplifies them.
Industry-Specific Use Cases
Finance
Financial institutions live under SOX 404 and, in Europe, DORA.
Auditors want evidence of role-based access changes and recovery testing. With Acsense, every admin action ties to an approval, and nightly DR reports prove compliance without manual prep.
Healthcare
Hospitals and insurers face HIPAA fines for untraceable changes.
With Acsense, every Okta update is captured immutably. If an outage disrupts patient portals, rollback restores access in minutes — protecting care delivery.
SaaS & Tech
Cloud-first companies in scope for NIS2 must prove operational resilience.
Acsense’s hot-standby option delivers <10-minute RPO and RTO, satisfying resilience mandates while keeping engineering teams focused on innovation.
Real-World Story: From Outage To Confidence
A global SaaS retailer managing multiple Okta tenants experienced repeated outages due to mis-scoped rules.
Git pipelines slowed recovery, and auditors flagged weak rollback evidence.
With Acsense:
- Every change was captured within 60 seconds.
- Rollbacks dropped from hours to under 10 minutes.
- SOX auditors passed controls using Acsense’s exportable reports.
Result: confidence instead of chaos.
Business Impact: Why Teams Choose Acsense
- Reduced outages – Misconfiguration downtime drops dramatically.
- Zero-downtime rollback – Instant restore capability.
- Consistency – Pre-prod and prod tenants remain in sync.
- Compliance savings – Audit prep reduced from weeks to minutes.
Speed with safety – Faster releases without Git overhead.
Acsense Vs. Git-Centric Alternatives
Capability | Acsense | Git/Terraform |
Storage | Immutable, encrypted WORM backups | Commits only |
Approvals | Native ITSM integration (ServiceNow/Jira) | Pull requests |
Rollback | One-click tenant/object restore | Revert + redeploy |
Drift Detection | Visual diff + sandbox seeding | Manual scripting |
Recoverability | Automated nightly tests + hot standby | None |
Security | No repos/tokens to guard | Repo secret exposure |
Takeaway: Acsense is purpose-built for IAM resilience, not code management.
Future Outlook: Why IAM Change Resilience Matters
IAM is now a board-level issue.
Gartner’s Identity-First Security research positions identity as the new security perimeter — making resilience essential.
As IAM change velocity grows, enterprises that continue relying on Git pipelines will face:
- More outages.
- Rising compliance risk.
- Longer recovery times.
Acsense’s approach — continuous capture, ITSM-native approvals, instant rollback — future-proofs IAM against both operational and regulatory shocks.
Conclusion: Secure Every Okta Change
Change velocity is only accelerating. Without the right approach, IAM admins risk outages, breaches, and failed audits.
With Acsense Change Management, you get:
- Real-time capture and rollback
- Sandbox testing and safe promotion
- ITSM-native approvals
- Immutable, compliance-ready evidence
👉 Contact us to learn more or schedule a demo today.
FAQ
Q1. What is change management in Okta?
Change management in Okta ensures every configuration update is tracked, approved, and reversible — reducing risk and meeting compliance.
Q2. Why avoid Git pipelines for IAM change management?
Git pipelines were designed for developers, not IAM admins. They expose secrets, slow rollbacks, and lack repeatable audit evidence.
Q3. How does Acsense improve audit readiness?
Acsense generates immutable data captures and nightly health reports, mapping every Okta change to approved ITSM tickets.
Q4. Can I roll back a single Okta object?
Yes. Acsense lets you restore a single object or an entire tenant instantly, with no downtime.
Q5. What RPO/RTO does Acsense deliver?
With an optional hot standby tenant, Acsense delivers <10-minute RPO and ~10-minute RTO.
Q6. How does Acsense prevent configuration drift?
Visual diffs and sandbox replication catch drift before it causes outages.
Q7. Can Acsense integrate with CI/CD pipelines?
Yes, Acsense can complement CI/CD for teams that want Git workflows in parallel, while eliminating reliance on repos and tokens.
Q8. How is data secured in Acsense?
Data is encrypted, air-gapped, and stored in immutable WORM-sealed vaults under ISO 27001-certified operations.
