Okta SSO accounts hit by vishing describes voice-phishing attacks where threat actors trick users into approving MFA during live calls. These attacks bypass MFA through social engineering, creating downstream operational and recovery risk even after access is restored.
TL;DR
Recent reports confirm Okta SSO accounts hit by vishing, where attackers bypass MFA through live phone-based social engineering. While access can often be regained, organizations struggle to validate what changed and restore authentication safely. The real lesson isn’t panic—it’s preparation, recovery readiness, and identity validation.
Table of Contents
- What Okta SSO Accounts Hit by Vishing Really Means
- How Okta SSO Credentials Bypass MFA in Vishing Attacks
- Why These Attacks Matter Beyond Initial Access
- What Okta and Media Have Confirmed
- The Hidden Recovery Gap After Identity Compromise
- What Okta Teams Should Validate After an Incident
- How Organizations Reduce Identity Downtime
- Conclusion: Turning Awareness Into Readiness
What Okta SSO Accounts Hit by Vishing Really Means
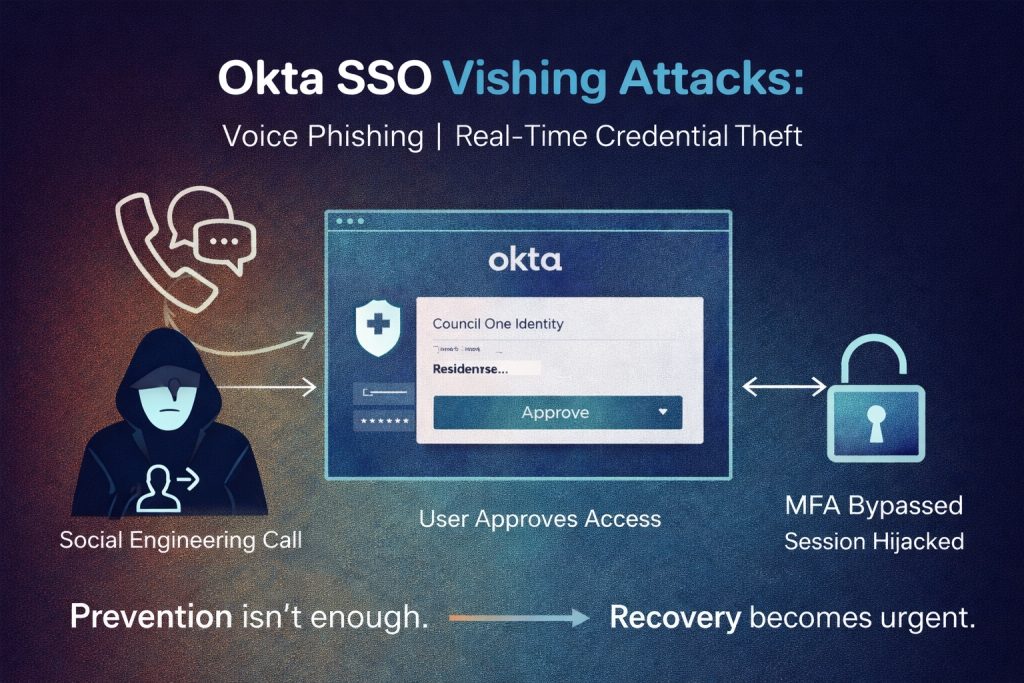
In early 2026, multiple security outlets reported Okta SSO accounts hit by vishing, a wave of identity-focused attacks combining voice phishing with real-time credential interception.
These incidents are not software vulnerabilities.
They are human-led attacks that exploit trust during live phone calls.
Attackers pose as IT or support staff and guide users through authentication steps in real time.
The user believes they are resolving an issue.
Instead, they are approving access.
This matters because modern identity systems sit at the center of enterprise operations.
When identity is compromised, access to email, SaaS applications, and internal systems can follow quickly.
The promise of MFA has always been protection.
These attacks show the limits of that promise when humans are involved.
The key question for security leaders is no longer “Can MFA be bypassed?”
It is “How quickly can we recover and validate identity after it happens?”
How Okta SSO Credentials Bypass MFA in Vishing Attacks
Reports confirm that attackers are using custom phishing kits designed for live vishing scenarios, rather than traditional email-based phishing.
Okta’s Threat Intelligence team has described how modern phishing kits dynamically adapt authentication pages in real time, synchronizing what the victim sees with what the attacker says on the phone. This allows attackers to capture credentials and MFA tokens during active sessions.
Media coverage explains that these kits can:
- Intercept login credentials and MFA codes as they are entered
- Update phishing pages dynamically based on the attacker’s script
- Guide victims through approvals that appear legitimate
Help Net Security reports that these vishing-friendly phishing kits are now widely available and specifically optimized for identity platforms like Okta SSO.
This explains why Okta SSO credentials bypass MFA in these scenarios. The system works as designed. The user approves the request.
Why These Attacks Matter Beyond Initial Access
The immediate concern is unauthorized access.
The larger concern is what happens next.
Okta SSO acts as a central gateway to enterprise systems.
Once attackers gain access, they may:
- Access downstream SaaS applications
- Modify group memberships or assignments
- Create persistence through additional identities
- Trigger extortion or data-theft scenarios
BankInfoSecurity reports that campaigns linked to groups such as ShinyHunters involve identity theft followed by extortion attempts once access is confirmed.
Importantly, none of the reporting suggests a breach of Okta’s core infrastructure. Instead, attackers exploit human trust and real-time interaction.
The damage comes from uncertainty.
Teams regain access—but do not know what changed.
What Okta and Media Have Confirmed
Across multiple outlets, the facts are consistent:
- Okta confirmed the existence of adaptable phishing kits designed for live vishing scenarios
(Okta) - IBM X-Force Exchange documented large-scale identity theft campaigns targeting Okta SSO using human-led social engineering
(IBM X-Force Exchange) - CyberScoop reported that attackers claim access to hundreds of organizations through SSO-focused vishing campaigns
(CyberScoop) - Industrial Cyber and other outlets describe these campaigns as active and ongoing
(Industrial Cyber)
The consensus: this is not a one-off event. It is a repeatable attack model.
The Hidden Recovery Gap After Identity Compromise
Most organizations focus on detection and containment.
Fewer focus on identity recovery.
After access is regained, teams must answer difficult questions:
- Which apps were accessed?
- What configurations changed?
- Are authentication flows behaving as expected?
- Can we trust current access state?
Without clear answers, teams delay decisions or take drastic actions.
This uncertainty is what creates operational downtime and, in some cases, pressure to pay extortion demands.
Identity incidents do not end when credentials are reset.
They end when trust is restored.
This is where identity resilience becomes critical.
https://acsense.com/blog/okta-disaster-recovery-plan-a-practical-guide-for-2025

What Okta Teams Should Validate After an Incident
A simple validation checklist helps reduce risk after vishing-based compromise:
Post-Incident Identity Validation Checklist
- Review admin and privileged account activity
- Validate SSO application assignments
- Confirm group memberships and role mappings
- Test authentication flows for critical apps
- Audit recent configuration changes
- Document known-good identity state
Teams that skip these steps often discover issues weeks later—during audits, outages, or user complaints.
How Organizations Reduce Identity Downtime
Prepared organizations treat identity like infrastructure.
They assume compromise is possible.
They plan for recovery.
Leading teams focus on:
- Continuous visibility into identity state
- Known-good recovery points
- Tested recovery workflows
- Clear ownership during incidents
This approach reduces downtime, limits uncertainty, and restores confidence faster.
This is the philosophy behind IAM Resilience—ensuring identity systems can be restored, validated, and trusted after disruption.
Conclusion: Turning Awareness Into Readiness
Okta SSO accounts hit by vishing highlight a hard truth.
Prevention alone is not enough.
These attacks succeed because they exploit human trust. The damage persists because recovery is complex.
Organizations that invest in identity recovery readiness respond faster, restore trust sooner, and reduce operational risk.
If you want to understand how teams are preparing for identity recovery scenarios:
- Contact us to learn more
- Schedule a demo
People-Also-Ask (FAQ)
Can MFA really be bypassed in Okta vishing attacks?
Yes. Attackers manipulate users into approving MFA during live calls, bypassing protections through social engineering rather than technical exploits.
Is Okta itself breached in these attacks?
No. Reports indicate attackers exploit users, not Okta’s core infrastructure.
What is vishing in cybersecurity?
Vishing is voice phishing—using phone calls to trick users into revealing credentials or approving access.
Why is recovery difficult after identity compromise?
Teams often lack visibility into what changed, making it hard to restore trust and validate access.
How can organizations reduce identity recovery time?
By preparing recovery plans, maintaining known-good identity states, and testing recovery workflows.
