The Shared Responsibility Model: The Critical Role of IAM Resilience in Cloud Security
With the increasing number of cyber attacks and data breaches in the news, it’s more important than ever to make sure that your company’s IT infrastructure is secure.
And if you’re like most IT and security professionals, you’re probably aware of the Shared Responsibility Model (SRM) and the importance of Identity and Access Management (IAM) resilience in cloud security.
As organizations increasingly adopt cloud computing services, they face the challenge of understanding and implementing the Shared Responsibility Model (SRM) for cloud security.
In this blog post, we will delve into the nuances of the SRM, examine the importance of Identity and Access Management (IAM) resilience, and provide unique insights into how organizations can maximize their cloud security posture.
Understanding The Shared Responsibility Model (SRM)
- The SRM divides the security responsibilities between the Cloud Service Provider (CSP) and the cloud customer.
- The CSP is responsible for security “of” the cloud, which includes physical facilities, hardware, and infrastructure.
- The customer is responsible for security “in” the cloud, encompassing network controls, IAM, application configurations, and data.
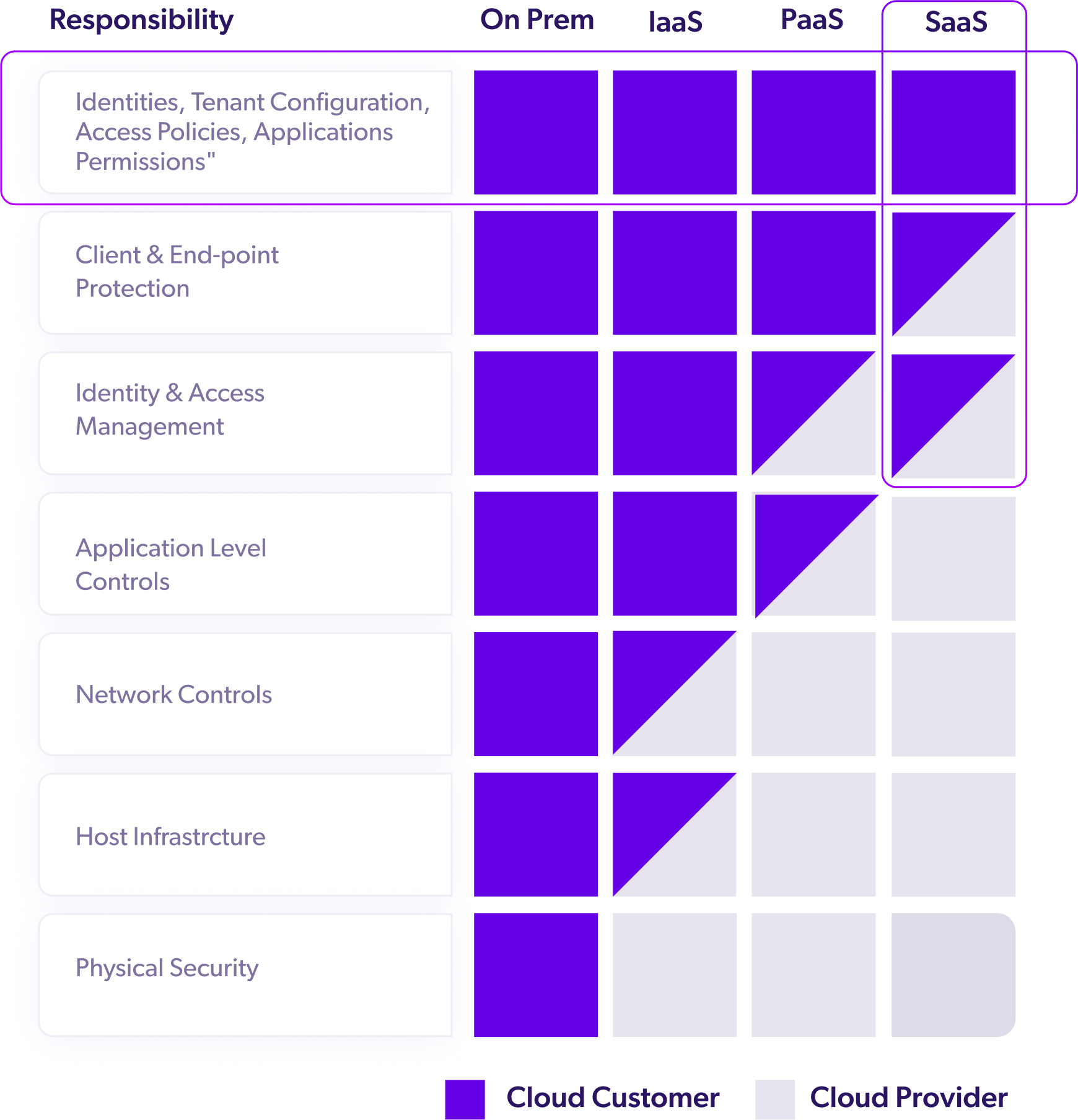
The Division of Responsibilities Varies Based on The Service Model:
- Infrastructure as a Service (IaaS):
The CSP handles the physical data center, networking, and servers. - Platform as a Service (PaaS):
The CSP manages patching and maintaining operating systems, in addition to IaaS responsibilities. - Software as a Service (SaaS):
The customer configures application settings while the CSP controls everything else.
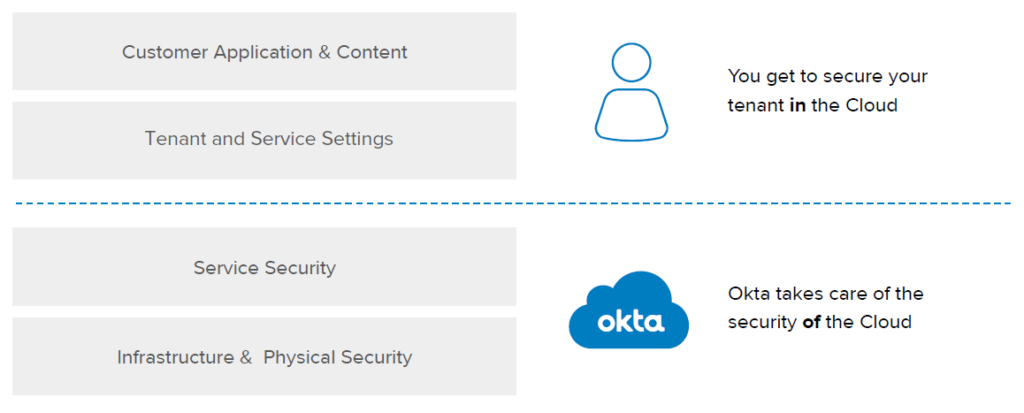
So, how does this apply to your role as a cloud customer with regard to your cloud IAM solution?
In a cloud IAM context, you are responsible for:
- Your data
- Your Devices
- Your Identities
For instance, let’s say you use Okta as your IAM provider.
Your responsibilities will include “Integrating applications and granting the correct permissions to your users, disabling accounts when employees are terminated, enforcing multi-factor authentication, properly configuring and monitoring the authentication policies required to protect your data, reviewing activity data in the system log to ensure users are following your policies, and monitoring your Okta tenants for attacks.”
Not only that, though.
You’ll also be responsible for maintaining access continuity. Okta (and other cloud IAM providers for that matter) are not responsible under the SRM for backing up your Okta tenants or ensuring your access.
That’s on you as the cloud customer.
Data-Driven Insights on IAM Resilience:
Organizations should consider the following insights and examples to bolster their IAM resilience:
- Strong authentication:
Two-factor or multi-factor authentication (2FA or MFA) significantly reduces the risk of unauthorized access. For example, Google reported that enabling 2FA blocked 100% of automated bot attacks, 96% of bulk phishing attacks, and 76% of targeted attacks (Google). - Least privilege principle:
Granting users the minimum necessary permissions reduces the potential impact of compromised accounts. A study by Varonis revealed that 53% of companies had more than 1,000 sensitive files accessible to all employees, emphasizing the need for proper access control (Varonis). - Regular audits and monitoring:
Continuously monitoring user activity and conducting periodic access reviews can help identify and rectify potential security risks. The 2020 Data Risk & Security Report by SecureCircle found that 89% of security incidents involved insider threats, highlighting the importance of monitoring and auditing IAM processes (SecureCircle). - Automated IAM solutions:
Implementing automation in IAM processes, such as provisioning and deprovisioning user accounts, can significantly reduce human error and enhance security. A Ponemon Institute survey found that 51% of IT professionals believed automation would improve their organization’s security posture (Ponemon Institute). - Employee training:
Educating employees on secure access practices and potential threats can reduce the risk of security breaches due to human error. A study by the SANS Institute discovered that organizations with continuous security awareness training experienced a 50% reduction in phishing susceptibility (SANS Institute). - Rapid Recovery and Business Continuity:
Include immediate restore capabilities, reducing the time and impact of system outages.A comprehensive business continuity plan must also address the potential single point of failure that SaaS-based access management tools can represent. Security and risk management leaders responsible for IAM should prepare for the possibility of their SaaS IAM tool becoming unavailable and develop a detailed plan for restoring services.
IAM Resilience: The Key to Cloud Security:
IAM resilience is essential for maintaining a secure cloud environment and allowing for business continuity in the event of a security breach.
But what is IAM resilience?
Under the shared security responsibility model, it involves implementing robust authentication and authorization processes, managing user access, and swiftly recovering from security breaches or misconfigurations.
A resilient IAM system is crucial in ensuring organizations fulfill their responsibilities within the cloud security shared responsibility model, as 99% of cloud security failures are predicted to be the customer’s fault through 2025 (Gartner).
What Cloud Customers Are Responsible For Under the Shared Responsibility Model in the Cloud
Figuring out where your responsibility under the cloud security shared responsibility model begins and where the CSP’s responsibility ends isn’t always as simple as it seems.
As Cloud Security Alliance notes,
“The key to a successful security implementation in a cloud environment is understanding where your provider’s responsibility ends, and where yours begins. The answer isn’t always clear-cut, and definitions of the shared responsibility security model can vary between service providers and can change based on whether you are using infrastructure-as-a-service (IaaS), platform-as-a-service (Paas), or SaaS (software as a service).”
So, what are you to do?
Crowdstrike offers five best practices to ensure you’re holding up your end of the shared responsibility model, including:
- Reviewing the SLA
- Prioritizing data security
- Ensuring robust identity and access management
- Embracing DevSecOps process and roles
- Identifying a trusted cybersecurity partner
Maximizing IAM Resilience and Cloud Security:
To maximize the resilience of your organization’s IAM systems in the cloud, consider Acsense’s Gartner Cool Vendor solution.
Acsense’s IAM Resilience platform offers enterprises advanced protection and swift recovery, ensuring IAM resilience and minimizing downtime. Our platform empowers IT, security and GRC leaders to actively safeguard and quickly recover from cyberattacks or misconfigurations against identity and access management systems, reducing associated costs and downtime.
Don’t wait until it’s too late – safeguard your organization’s IAM infrastructure under the cloud shared responsibility model with Acsense today.

