Oktapus Hacker Group: Essential IAM Strategies and Best Practices
The group, referred to as Octo Tempest by Microsoft and also known as Oktapus, Scattered Spider, and UNC3944 by other experts, adopts a range of social engineering strategies.
These tactics are used to penetrate corporate networks, expropriate sensitive data, and coerce organizations into paying ransoms, as per insights from Microsoft Threat Intelligence.
Oktapus started its malicious acts in early 2022.
It targeted mobile and business organizations to execute phone number ports or SIM swaps.
The group sold these SIM swaps to other criminals and took over accounts of high net-worth individuals to steal their cryptocurrency.
Oktapus has been termed one of the most dangerous financial criminal groups in operation.
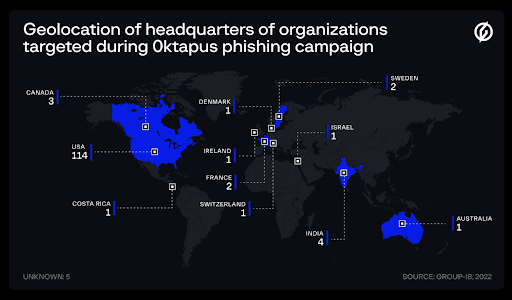
The group, known as “0ktapus,” earns its name by targeting users of Okta’s Identity and Access Management services.
It directs victims to deceptive pages resembling legitimate ones to steal Okta credentials.
Their methods are definitely not brand-new. But what is interesting is how it turned into a big-scale show.
The threat actor targeted renowned tech giants like Twilio and Cloudflare.
Employees claimed to receive phishing text messages that lured them to enter credentials on a malicious website.
The messages mentioned expired passwords and schedule changes, directing recipients to fake domains.
The attackers demonstrated sophisticated abilities and reflected a well-organized and sophisticated approach.

Read the article to learn more about the recent threat actors and some effective Oktapus hacker group defense strategies.
Oktapus Hacker Group Cybercrime Playbook
Oktapus is a highly organized group known for its extensive cyberattacks. They employ various tactics, techniques, and procedures (TTPs) to gain unauthorized access to organizations.
One notable method they use is social engineering, especially targeting technical administrators like support and help desk personnel.

The individuals have targeted over 130 organizations, stealing the credentials of nearly 10,000 employees.
The organizations targeted were primarily based in the U.S., with the U.K. and Canada following suit. Most companies belonged to the I.T. sector, specializing in the cloud and software development sector. As of now, they are still actively pursuing various tech and video game companies.
Oktapus researches the organization and impersonates victims to trick administrators. It performs actions like password resets and changing multifactor authentication methods. The attackers often mimic new employees to blend into regular onboarding processes.
Their initial access methods include:
- Social engineering calls to employees, convincing them to install monitoring tools or visit fake login portals.
- Manipulating help desks into resetting passwords or modifying authentication methods.
- Purchasing employee credentials from criminal markets.
- Phishing employees via SMS with links to fake login portals.
- Exploiting pre-existing access in telecom and outsourcing organizations for activities like SIM swaps.
Having achieved their initial achievements, Oktapus adopted a more assertive approach.
The group expanded its focus from late 2022 to early 2023. They used their expertise and acquired data to escalate their goals, targets, and methods. Soon after, the attackers turned to cable telecommunications, email, and technology organizations.
During this phase, Oktapus extorted money from victim organizations.
The attackers also targeted individuals with threats to extract corporate access credentials.

The Oktapus group employs advanced tactics to gain access to targeted environments.
It identifies documents related to the network architecture, employee onboarding, and password policies.
Oktapus had a straightforward goal: get Okta identity credentials and two-factor authentication (2FA) codes from targeted organization users. The information would allow attackers to access enterprise resources without authorization.
The group uses security personnel accounts to turn off security features, deploys malicious tooling, and steals sensitive files. Modifying mailbox rules helps suppress alerts and allows them to manipulate security products without raising suspicion.
What makes Oktapus notable is that it successfully compromised well-known organizations despite using basic methods. Moreover, once an organization was compromised, the attackers launched supply chain attacks.
It highlights their deliberate and careful planning behind the assault.
Oktapus Hacker Group Defense Strategies and Best Practices
Social engineering and phishing attacks have been used for years to trick unsuspected victims.
While various malicious activities exist, social engineering accounts for 98% of cyberattacks.
The Oktapus hacking group employed these techniques to execute malicious activities. It underlines the urgency to adopt best practices to protect your company.
Following are some established and tested strategies to help you:
1. Create a Backup Strategy, aka Disaster Recovery Plan
In the event of an Oktapus hacker group attack or data breach, having reliable backups can expedite the recovery process. A backup and disaster recovery entails periodically creating or updating additional copies of files, storing them at more than one location, and accessing those copies to resume business operations in case of a cyberattack.
2. Business Continuity Plan
A business continuity plan (BCP) is a strategy playbook designed to assist an organization in maintaining or resuming its services during a cyberattack. It involves the following:
- Identifying and analyzing security risks and possible dangers to your organization’s vital infrastructure.
- Conducting a business impact study to assess the possible impact of interruptions and define recovery objectives.
- Implementing strategies and recovery plans can assist the organization in responding successfully to a cyberattack.
- Regularly test the organization’s cyber incident response plans to ensure their effectiveness. This includes ensuring that they work correctly and assist and recover your business’s vital functions in the event of a cyberattack.
3. Ensure Restricted Access
Implementing restricted access within a company is among the powerful Oktapus hacker group defense strategies.
You can carefully control who has access to sensitive information and critical systems. It will help ensure you do not fall victim to cyber-attacks. Restricted access acts as a barrier. It will make it more challenging for malicious actors to infiltrate and compromise valuable data.
It involves a systematic process:
- Conduct a comprehensive audit of existing access permissions. Identify who has access to data and resources.
- Categorize roles to define specific access levels based on job responsibilities. Clearly outline who needs access to critical systems and sensitive information.
- Adopt RBAC principles to assign access rights according to job roles. It ensures that employees can access their responsibilities. But, it will restrict access to unnecessary systems or data.
Establish a routine for regular access reviews.
Reassess and update access levels based on changes in job roles or employee status. It can help you create a structured and secure access environment. Ultimately, you will minimize the risk of unauthorized access and enhance overall cybersecurity resilience.
4. Craft an Incident Response Plan
A well-thought-out incident response plan is essential to prevent phishing attacks effectively.
The plan involves the necessary steps and actions to respond to a security incident.
A robust incident response plan should have the following key steps:
- Recognize the source and nature of the incident to determine its scope and severity.
- Isolate the affected system or network promptly to prevent damage or spread of the attack.
- Collect and analyze data to uncover the root cause of the incident and evaluate the extent of the damage incurred.
- Remove any access points or malicious software from the affected systems.
- Restore the system, network, and data to their state before the attack to decrease downtime.
Conducting a post-incident review to identify weaknesses in the response plan.
It will help implement necessary improvements to prevent similar incidents in the future.
5. Building a Resilient Identity and Access Management (IAM) Strategy
A well-thought IAM resilience strategy is the best defense to secure your organization.
An IAM Resilience Platform for access continuity coupled with fundamental IAM best practices can enhance defenses by enforcing strict access controls, implementing multi-factor authentication (MFA), and regularly monitoring user permissions.
IAM automation for account provisioning and de-provisioning, coupled with encryption measures, adds an extra layer of protection. Additionally, including IAM in incident response planning ensures a comprehensive defense, emphasizing clarity in communication to enhance organizational resilience against potential threats.
6. Multi-factor Authentication
Gone are the days when passwords could solely safeguard your online presence.
A study shows that compromised credentials enabled 19% of data breaches in 2023. Simply put, you may become a cyberattack victim if someone figures out your password.
Multi-factor authentication (MFA) is a crucial strategy for improving security. It requires additional authentication elements from users to access data.
MFA includes three key factors:
- Something you know (knowledge): Passwords, PINs, or combinations fall into this category.
- Something you have (possession): Devices like USB drives or token devices contribute to this factor.
- Something you are (inherence): It could be unique biometrics such as fingerprints or facial recognition.
You can opt for a two-factor authentication method and integrate any of the mentioned processes.
Since many account takeover attacks stem from deceptive emails and websites, implementing MFA can help block unauthorized access.
7. Advanced Network Monitoring
Cybercriminals launch a new phishing attack every 39 seconds.
You may overlook the subtle signs of malicious activity without monitoring and timely responses. It can present opportunities to exploit vulnerabilities in your system.
Advanced network monitoring actively gathers and analyzes network data to identify security issues.
It monitors logs for unusual patterns and correlates events with threat intelligence.
Advanced network monitoring goes beyond mere detection.
It alerts I.T. administrators to potential threats and enables swift actions.
Thus, it can be a proactive defense mechanism for your company.
8. Promote Awareness Training
Employees are the first line of defense to prevent cyber attacks.
Their regular interaction with messages, emails, and online content makes them the initial target.
Approximately 42% of employees admit clicking on an unknown link, exposing personal data, or downloading an anonymous file. Human error is the reason behind about 72% of cybersecurity breaches.
As a result, the human factor is important to identify suspicious activity and report potential threats.
Spreading awareness about phishing risks is one of the most effective Oktapus hacker group defense strategies.
Regular training sessions can help employees gain insights into cyber attacks and their common methods.
Proper knowledge will allow them to exercise caution and practice the best strategies.
Reliable technical defenses and a security culture are essential to protect your organization.
But how would you know whether your planned, proactive methods fare well during a cyber attack?
Consider organizing a simulated phishing campaign to check how safe your company is.
It will also highlight the weak points and tell you what you could do better.
Conclusion
In the context of rising cyber threats and identity thefts, even large tech companies are not immune to incidents like the 0ktapus attacks. This situation highlights the critical need for robust cybersecurity practices in managing Identity Access Management (IAM) systems.
Acsense stands at the forefront of addressing these challenges.
Our IAM Resilience Platform offers an effective shield against such threats.
We provide continuous, immutable backups and flexible recovery options, ensuring effortless data security.
The platform’s design for seamless continuity dramatically reduces downtime during cyber incidents.
Moreover, with simplified compliance tailored to standards like HIPAA and ISO 27001, Acsense helps fortify your cybersecurity infrastructure against evolving threats.
Our solutions are not just about protection but also about empowering organizations to manage their IAM responsibilities effectively.
For a comprehensive approach to IAM resilience and to learn more about how Acsense can support your cybersecurity strategy, Book a demo today!



