What is NIST?
NIST(National Institute of Standards and Technology) is a non-regulatory government agency.
It helps businesses understand, manage, and reduce cybersecurity risks and protect their crucial data and networks. It offers a voluntary framework of best practices to help you decide where to focus your time and resources for cybersecurity protection.
Within the NIST framework, IAM plays a key role in ensuring business security.
This blog will teach us to create a robust cybersecurity structure by aligning your IAM practices with the NIST Cybersecurity framework.
NIST’s Role and Activities in IAM
NIST conducts the below activities to advance the state of identity and access management.
- Conducting focused research on emerging technologies and their impact on existing standards.
- Leading the development of national and international identity and access management standards.
- Providing guidance, best practices, profiles, and frameworks for enhanced, interoperable solutions.
- Addressing authentication and authorization within the Internet of Things (IoT).
- Evolving identity and access management standards, guidelines, and resources.
- Producing example solutions that integrate identity management and cybersecurity requirements.
- Enhancing understanding of new technologies for effective implementation.
NIST: Mission & Focus on Cybersecurity and Standards
The National Institute of Standards and Technology promotes US innovation and industrial competitiveness.
NIST achieves its mission by strengthening innovation and industrial competitiveness by providing leadership and support in developing measurement standards and technology.
The NIST Cybersecurity Framework helps businesses understand, manage, and reduce their security risk regardless of size. With NIST, you get best practice guidelines that help you to decide what needs your time and focus.
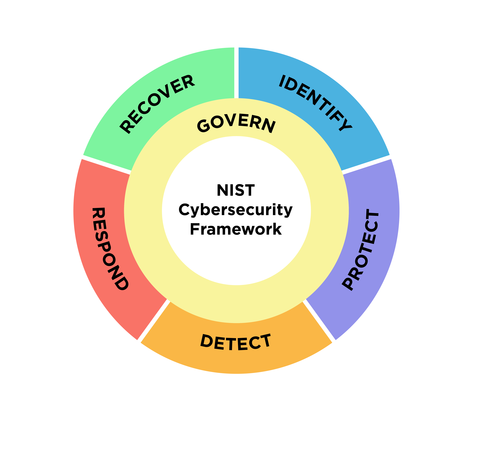
NIST Framework
The NIST framework consists of five main functions:
- Identify: Understand and prioritize cybersecurity risks to manage them effectively.
- Protect: Develop and implement safeguards to ensure the delivery of critical infrastructure services.
- Detect: Implement activities to identify the occurrence of a cybersecurity event.
- Respond: Develop and implement response activities to mitigate the impact of a detected cybersecurity event.
- Recover: Implement recovery plans to restore capabilities or services impaired due to a cybersecurity event.
Credit: N. Hanacek/NIST
Fundamental NIST Principles
NIST offers a robust framework for Identity and Access Management (IAM), offering a set of principles that prioritize privacy, security, usability, and more.
The fundamental NIST principles for IAM below discuss the implementation process, highlight the benefits, and address the challenges.
1. Privacy and Security
NIST emphasizes the crucial balance between privacy and security.
It urges organizations to safeguard sensitive information and ensures robust and effective access management practices.
2. Foster Equity and Individual Choice
IAM must be designed with fairness and individual autonomy in mind.
NIST encourages organizations to give users choices regarding their digital identities and access preferences, fostering a sense of equity.
3. Promote Usability and Accessibility
User-friendly and accessible IAM solutions are vital for successful implementation.
NIST recommends making IAM processes intuitive and available to users with diverse needs, ensuring seamless access management experiences.
4. Enhance Interoperability and Standardization
NIST advocates for interoperability and standardization in IAM solutions to facilitate smoother integration and collaboration. Aligning IAM practices with common standards promotes consistency and compatibility.
5. Better Measurement and Transparency
Regularly measuring and assessing the effectiveness of IAM systems is a mandate.
But when you implement NIST principles, your organization is better placed to evaluate and improve its security posture.
Reason: NIST encourages transparency in IAM processes.
Applying NIST Cybersecurity Principles to Enhance IAM Resilience
When organizations implement NIST principles for IAM, they fortify their IAM framework and enhance their security.
They also ensure organizations meet the required compliance requirements and offer better user experience.
Here are some ways to guide you through the implementation process:
1. Aligning IAM Practices with NIST Guidelines
Begin by understanding and aligning your IAM practices with the fundamental NIST principles.
You must review current processes, policies, and technologies.
This will help you to identify the areas where you need to align your IAM practices with NIST guidelines.
2. Organizing Gap Analysis and Risk Assessments
When implementing NIST principles, Identifying potential vulnerabilities and shortcomings in your current IAM strategy by thoroughly assessing the risk factor and gap analysis should be your first step.
Reason: This step will help you make an informed decision.
3. Selecting Best Practices and Implementing Relevant Controls
Choose controls and best practices that align with NIST principles and address the identified gaps.
MFAs, access controls that are defined per roles, and other security measures are part of this implementation step.
4. Continuously Monitoring and Improving IAM Posture
Establishing a robust monitoring system will help you keep track of IAM activities.
However, you must regularly assess and refine your IAM strategy based on emerging threats, technological advancements, and changes in organizational requirements.
Advantages of Using NIST for IAM
There are numerous advantages of using NIST for IAM.
Here are a few prominent ones.
1. Say No to Unauthorized Access
When you implement NIST principles, your IAM systems’ security is better.
Result: Reduced risk of unauthorized access and potential data breaches.
2. Better Your Compliance With Improved Regulations And Standards
When you implement NIST principles, you align your compliance requirements with different regulatory frameworks and industry standards. NIST ensures your organization meets or exceeds the required security benchmarks.
3. More User Experience And Increased Productivity
When implementing NIST principles, you prioritize usability and accessibility by offering a better user experience.
The result will be better satisfaction of your users and increase your employees’ productivity.
4. Cost Reduction Via Better System Integration And Efficiency
When you have IAM practices that are standardized, you will have processes that are streamlined.
Result: Reduction in operational costs and improved overall efficiency.
NIST Version 2.0
The National Institute of Standards and Technology (NIST) has recently released version 2.0 of its widely used Cybersecurity Framework (CSF), marking the first major update since its inception in 2014.
The new 2.0 edition is designed for audiences, industry sectors, and organization types – from the smallest schools and non-profits to the largest agencies and corporations — regardless of their degree of cybersecurity sophistication.
CSF 2.0 is not about one document. Curated on previous versions, it is a suite of resources which you can customize and use it individually or in combination depending on your organization’s required cybersecurity. In short, the new CSF 2.0 can be customized by your organization’s changing needs and capabilities.
The new 2.0 framework’s core is now organized around the five key principles of NIST along with the sixth function of Govern.
So now the new framework is based on six key functions:
- Identity
- Protect
- Detect
- Respond
- Recover
- Govern
When combined, these functions offer a detailed view of how organizations can manage their cybersecurity risk.
The release of NIST’s CSF Version 2.0 signifies a significant step in enhancing cyber resilience across diverse industries.
Initially crafted for critical infrastructure, the updated framework now extends its guidance to organizations of all sizes and sectors, regardless of their cybersecurity expertise.
Bridging the Gap: Acsense’s Solution to the IAM Recovery Challenge in NIST
The NIST framework – “In the realm of IAM, integrating NIST principles is paramount, especially in the dynamic digital landscape we navigate today.
The NIST framework, encompassing the functions Identify, Protect, Detect, Respond, and Recover, delineates a comprehensive approach to fortifying cybersecurity. This integration of IAM practices with NIST guidelines fosters improved security, regulatory compliance, enhanced user experiences, and optimized costs.
A recent insightful analysis by Eve Maler, a renowned digital identity futurist and strategist, as well as the co-inventor of foundational technologies like XML, SAML, and UMA, has shed light on a critical aspect of the NIST framework.
As a respected Privacy by Design Ambassador, her evaluation of the NIST Cybersecurity Framework in the context of IAM reveals a notable observation: while sectors like Identity Security Posture Management (ISPM), Classical IAM, Cloud Infrastructure Entitlement Management (CIEM), and Identity Threat Detection and Response (ITDR) effectively cover Identify, Protect, Detect, and Respond, the Recover function remains under-addressed in the IAM domain.
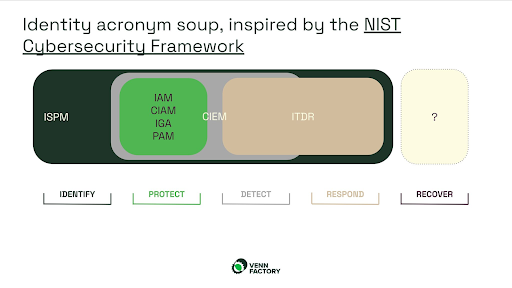
Addressing this gap, Acsense’s IAM Resilience Platform emerges as a comprehensive solution.
Our platform bridges this gap in the Recover function, an aspect that is often overlooked in traditional IAM systems.
By providing continuous backups, one-click granular recovery, and compliance assurance, Acsense enhances the resilience and operational continuity of identity management systems. Our platform is not just a response to the existing challenges but a proactive measure ensuring robust recovery capabilities, aligning perfectly with the NIST framework’s comprehensive approach.
Choosing Acsense’s IAM Resilience Platform means embracing a full-fledged IAM strategy that aligns with NIST’s best practices and addresses the nuances highlighted by experts like Eve Maler. We offer a solution that spans the entire IAM spectrum, transforming potential vulnerabilities into fortified strengths. For an IAM strategy that is resilient, adaptable, and ahead of the curve, explore how Acsense can redefine your approach to identity management.
Discover more by booking a call with us today.



