20 IAM Stats You Should Know!
Identity and Access Management (IAM) is the foundational framework ensuring the right individuals have appropriate access to crucial resources, emphasizing the importance of strategic IAM in today’s digital ecosystem.
Here’s a look at 20 essential IAM statistics that highlight the evolving nature of Identity and Access Management (IAM).
1. Market Growth and Adoption
- IAM Market Growth:
The global identity and access management market is projected to touch $23.8 billion by 2023. (Source: MarketsandMarkets)
Takeaway: The growing reliance on IAM solutions points to their increasing significance in today’s digital realm. - Biometric Authentication:
Anticipated to see a rise of 20% in 2023, biometric authentication is rapidly gaining traction. (Source: MarketsandMarkets)
Takeaway: Modern IAM systems integrating biometrics can offer enhanced security against breaches. - IoT Expansion:
By 2025, we’re looking at a world teeming with approximately 75.44 billion IoT devices. (Source: Statista)
Takeaway: With the IoT network expanding, IAM systems must adapt to safeguard these interconnected devices.
- Cyber Insurance Demand:
The cyber insurance market is set to burgeon, with projections hitting $14 billion by 2023. (Source: MarketsandMarkets)
Takeaway: The surge in cyber insurance adoption underscores the financial risks associated with cyber threats and the role of IAM in mitigating them. - IAM Software Adoption:
By 2023, 65% of large enterprises will be using identity and access management software to enhance security measures. (Source: Gartner)
Takeaway: The rapid adoption of IAM software underscores its importance in the modern security landscape. Organizations that have not yet integrated IAM solutions should consider doing so to stay competitive and secure in today’s digital world.

2. Authentication & Password Management
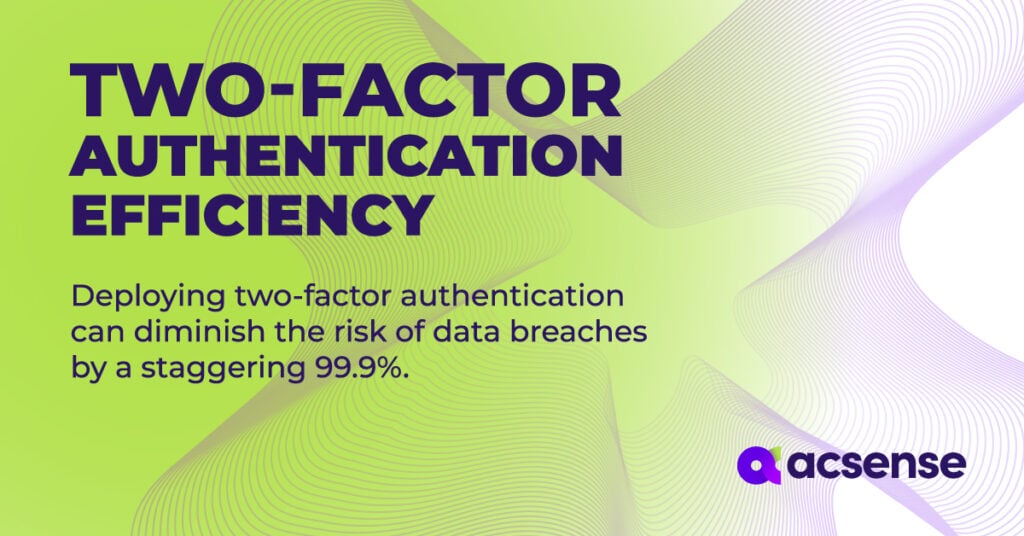
- Two-Factor Authentication Efficiency:
Deploying two-factor authentication can diminish the risk of data breaches by a staggering 99.9%. (Source: TechBeacon)
Takeaway: Incorporating two-factor authentication in IAM is no longer a luxury but a necessity. - Password Weakness:
A massive 80% of data breaches can be traced back to weak or stolen passwords. (Source: Verizon Data Breach Investigations Report)
Takeaway: IAM solutions focusing on robust password policies can drastically reduce vulnerability.
3. Breach Statistics & Impact
- Breach Detection Delay:
A concerning statistic reveals that organizations take an average of 197 days to detect a data breach. (Source: IBM)
Takeaway: Timely breach detection is imperative, urging IAM systems to integrate real-time monitoring capabilities. - Breach Containment:
Post detection, containing a breach still takes an average of 69 days. (Source: IBM)
Takeaway: Speedy response mechanisms within IAM strategies can mitigate further damage. - Breach Costs:
Breaches come with a hefty price tag, with the average cost spiraling to $3.86 million. (Source: IBM)
Takeaway: Investing in comprehensive IAM solutions can be cost-effective in the long run. - Cloud Data Breaches:
Alarmingly, one in every four organizations has experienced a cloud data breach. (Source: McAfee)
Takeaway: As cloud technologies become mainstream, IAM policies need to be extended and reinforced in cloud environments.

4. Financial Implications and Consequences
- Phishing Attack Costs:
The aftermath of a successful phishing attack can lead to average costs of $1.6 million. (Source: Wombat Security)
Takeaway: Strengthening IAM defenses against phishing is crucial, given its financial implications. - Insider Threat Costs:
Malicious insider threats can burn a deep hole in finances, with average costs reaching $11.45 million. (Source: Accenture)
Takeaway: IAM should closely monitor and regulate internal access to deter potential insider threats. - Small Business Vulnerability:
A grim reality for small businesses: 60% shut their doors within six months of a cyber attack. (Source: National Cyber Security Alliance)
Takeaway: Regardless of size, every business must prioritize IAM to ensure longevity and resilience against threats.

5. Operational Insights and Improvements
- Human Error:
A third of data breaches, or 33%, have human error at their root. (Source: Verizon Data Breach Investigations Report)
Takeaway: Integrating user education and training is a pivotal part of a holistic IAM approach. - Patch Delays:
In 2021, the timeline to patch a vulnerability stretched to an average of 70 days. (Source: SolarWinds MDR)
Takeaway: Prompt vulnerability management can bolster an organization’s IAM defenses. - Ransomware Rise:
The year 2022 saw ransomware attacks surging by a whopping 141%. (Source: CrowdStrike)
Takeaway: With ransomware on the rise, IAM systems must be fortified to counteract these specific threats. - Breach Preparedness:
A mere 14% of organizations claim to be fully prepared for a breach. (Source: Accenture)
Takeaway: Organizations must continually evaluate and update their IAM strategies to remain prepared for evolving threats. - Employee Training Necessity:
30% of phishing emails are opened (Source: Wombat Security). This highlights the effectiveness of phishing attacks and the importance of employee education and robust IAM systems to reduce the risk of a successful attack. (Source: Wombat Security)
Takeaway: Regular and comprehensive training is essential to ensure all employees are well-versed in cybersecurity best practices. - Mobile Security Concerns:
60% of organizations have experienced a security incident related to unsecured mobile devices. (Source: CheckPoint)Takeaway: With the proliferation of mobile device usage in enterprises, securing them becomes paramount. This statistic underscores the urgency for robust mobile-focused IAM solutions.

Final Thoughts on Identity and Access Management
Identity and access management stand as a pivotal aspect of contemporary cybersecurity.
Organizations need to stay updated with IAM trends and statistics to comprehend the ever-evolving threat landscape. By embracing best practices and understanding current data, they can fortify their defenses, safeguarding both themselves and their clientele from potential breaches.



