Strengthen Your Cybersecurity Against LAPSUS$
Insider threat attacks are rising.
The LAPSUS$ hacking group illustrates how even loosely organized hackers can significantly damage organizations using such techniques. The group has made tons of headlines for its cyberattacks. Their hacks into high-profile companies like Microsoft, SITEL, and T-Mobile surprised many.
Their goal?
Steal valuable data and threaten companies to make blackmail payments.
Do you need to be concerned?
Can you save yourself from potential LAPSUS $ attacks?
Yes, to both.
LAPSUS$ has followed a very targeted approach till now.
Learning more about them can help you implement the necessary measures to defend against LAPSUS$ cyber threats.
So, keep reading!
Who is LAPSUS$?
LAPSUS$ is a notorious hacking group, active since 2019.
It is known for its substantial funding and high level of organization. Its members hail from various countries across the globe. The group includes several juveniles and has a knack for exploiting the daily needs of users.
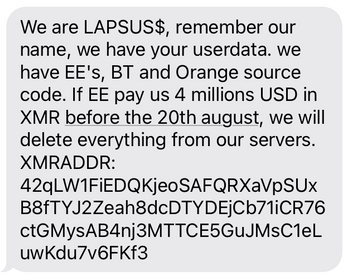
Their first activity was detected in underground forums in July 2021, with discussions of video game company breaches and targeting cryptocurrency accounts. The scope expanded and escalated to global companies and high-profile organizations.
What is unusual about them is that they do not hide – LAPSUS$ members brag about their hacks on the messaging app Telegram. The group garnered much attention for its unconventional infiltration into the IAM provider, Okta. They got remote access to a machine belonging to an employee of SITEL, a company subcontracted to offer customer service functions for Okta.
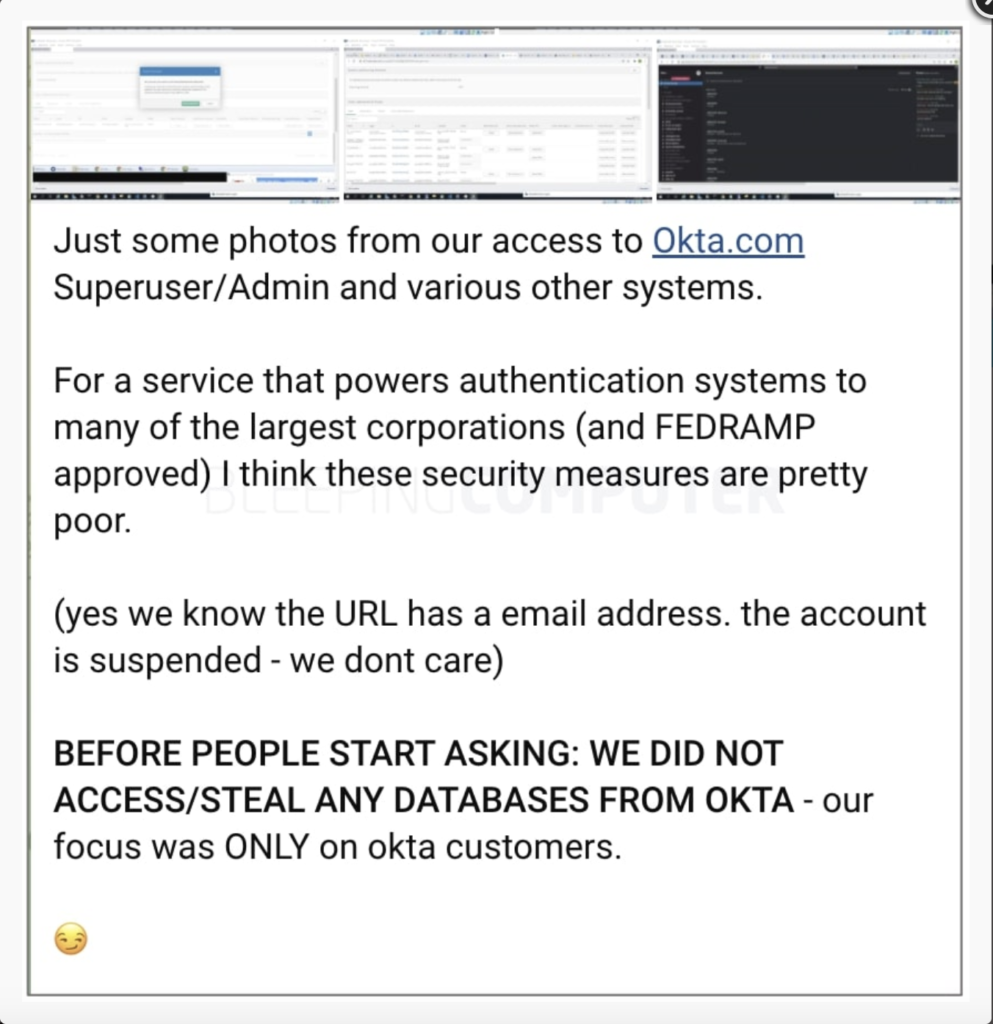
The breach details emerged two months later when a LAPSUS$ member shared screenshots of the internal systems on their channel. They have attacked several companies and leaked their information.
The London police have arrested multiple members suspected of being associated with the group.
Rumors say that the mastermind behind LAPSUS$ could be a 16-year-old from Oxford, England.
LAPSUS$ Attacks and Methods
LAPSUS$ initially focused on companies in South America and the UK.
They have expanded to include targets worldwide, like governments, phone companies, the tech sector, and the media. The hacking group gained notoriety with a ransomware attack on the Brazilian Ministry of Health in December 2021.
The attack jeopardized the COVID-19 vaccination data of millions in the country.
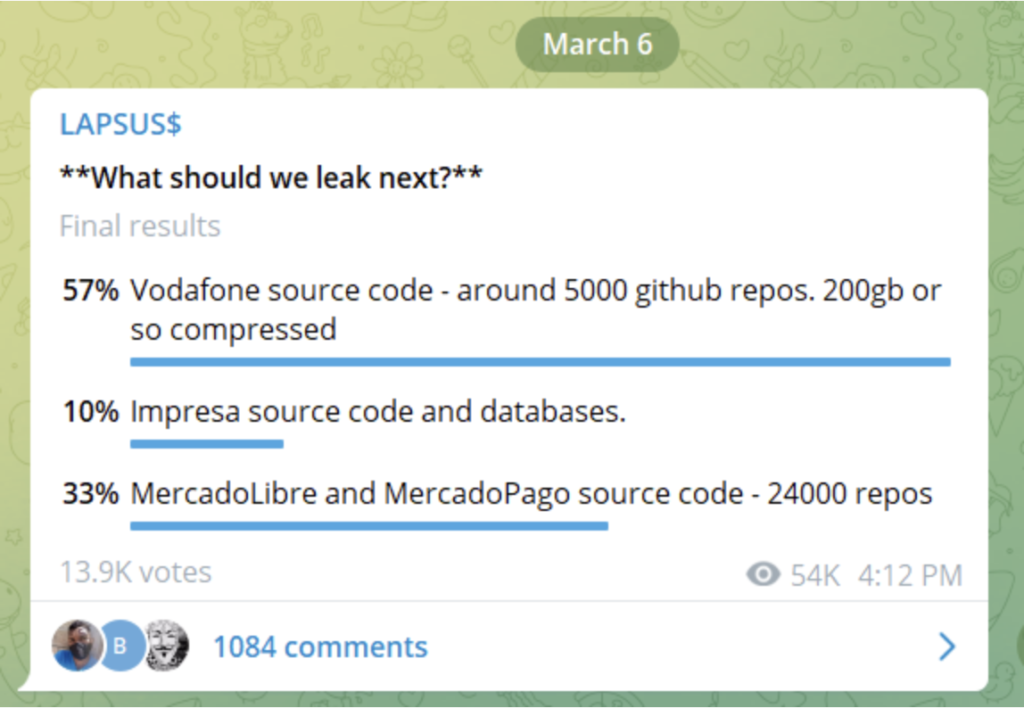
Source
Unveiling LAPSUS$ Tactics
Often described as “bold, illogical, and poorly thought out methods,” it has helped the group successfully breach companies. Here is how they did it: LAPSUS$ bought usernames and passwords, tricked some people on the inside, and broke into the secret computer codes and information.
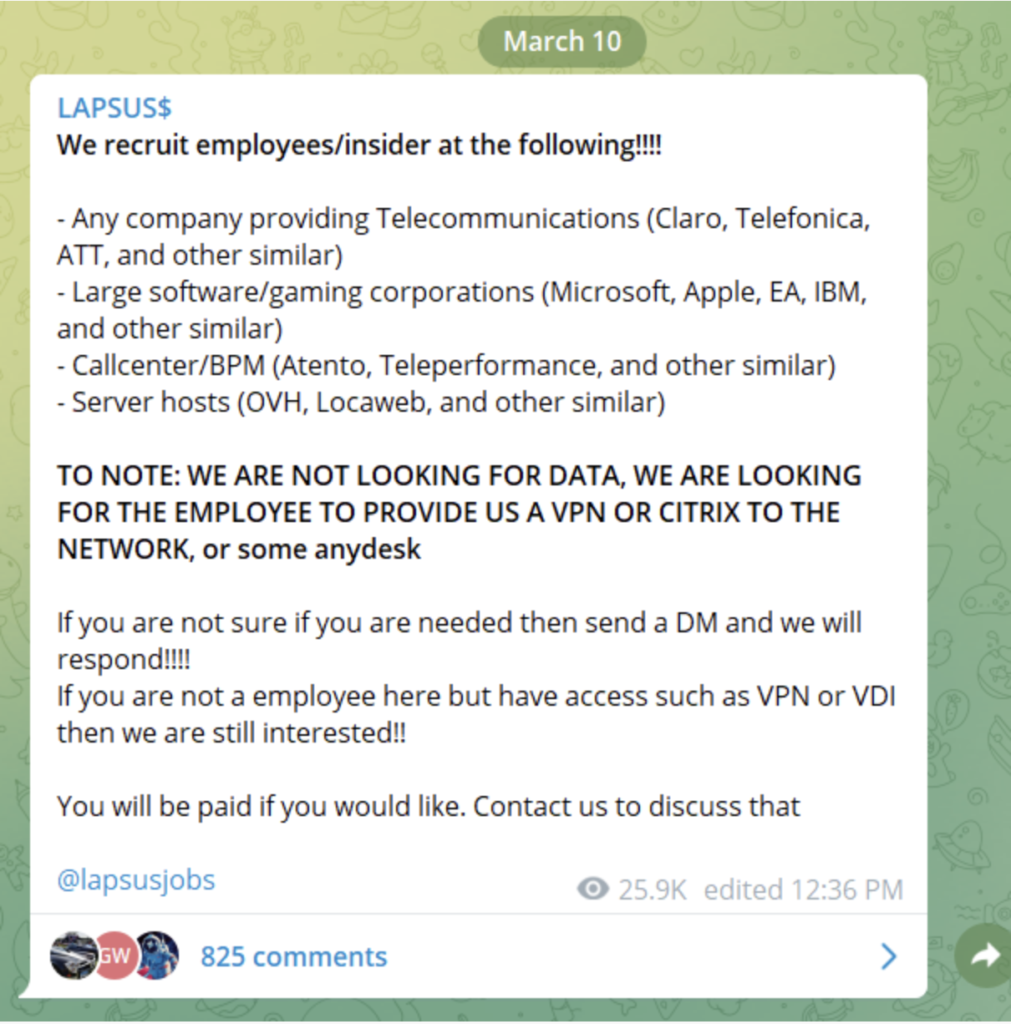
Source
1. Using Phone-based Social Engineering via SIM-swapping
LAPSUS$ hackers engaged with employees throughout the attack and employed various techniques and languages. They utilize spear-phishing and human vulnerability in initial access to entice employees and contractors into visiting deceptive sites.
Voice phishing became a valuable tool for impersonating trusted personnel over the phone and extracting personal information to reset complete account recovery procedures. SMS phishing was another effective strategy. The members delivered deceptive links to phones and legitimate domains where credentials were entered and used to change passwords.
2. Compromising personal and private accounts to gain access
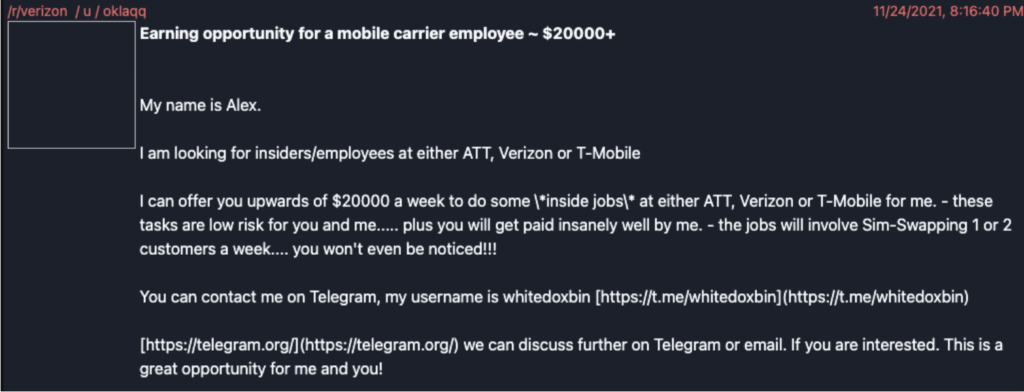
LAPSUS$ actively recruits employees from telecom, call center, software, or gaming firms.
They offer incentives to employees in exchange for VPN or RDP credentials.
Once they receive access, they exploit vulnerabilities, search code repositories for more credentials, and exfiltrate data. The group deletes systems and resources to trigger the incident response process.
Subsequently, LAPSUS$ actively participates in response calls and internal discussion chat forums.
Defend Against LAPSUS$ Cyber Threats with Integrated Backup and IAM Resilience
The Data Breach Investigation Report found that social engineering is behind 85% of breaches.
Consequently, adopting a holistic approach is crucial to raise awareness about security risks and discourage compromises.
Here are some essential strategies to defend against LAPSUS$ cyber threats:
1.Unified Backup and IAM Resilience Strategy
Companies can fortify their IT systems through a robust backup and recovery strategy.
Backing up crucial data and systems proves a safety net for potential breaches.
- Implementing a robust backup strategy is foundational in reinforcing your defense against breaches. By integrating backup with IAM resilience, organizations can create a more fortified barrier against cyber threats.
- Regular backups of critical data and systems form the backbone of this strategy. Ensuring these backups are intertwined with your IAM framework enhances both security and accessibility.
- Encryption of backup data is crucial. When combined with IAM controls, it adds a formidable layer of security, preventing unauthorized access even in the event of a breach.
- Regular testing of backup and recovery processes is vital. Integrating these tests within the IAM framework ensures not only the reliability of data recovery but also the integrity and compliance of user identities and access privileges.
2. Enable Multi-Factor Authentication
Multi-factor authentication requires multiple forms of verification.
The additional passwords help reduce the risk of unauthorized access.
- Protects against stolen or compromised passwords.
- Adapts security measures based on user behavior and contextual factors.
- It demands extra authentication and mitigates the effectiveness of phishing attacks.
3. Review your VPN Authentication
VPN authentication is one of the effective ways to protect your data from LAPSUS$ attacks.
- Allows you to fine-tune access controls and ensure only authorized personnel gain entry.
- Regular scrutiny can help detect unusual patterns or anomalies in VPN access.
- The strength and integrity of login credentials reduce the risk of compromised and weak passwords.
4. Leverage Password Authentication Tools
Integrating smart password authentication tools is a strategic investment to defend against LAPSUS$ cyber threats.
These essential components can safeguard sensitive information and maintain correct access controls.
- Helps enforce robust password policies to create and maintain secure and complex passwords.
- Continuous monitoring of password usage provides real-time insights into user activities.
- Includes features to detect and prevent brute force attacks.
5. Plan for Future Attacks
More than reliance on technology is required to tackle emerging cyber threats.
It is ideal to align security practices with business continuity management to foster an uncompromised technical environment.
- Security professionals must establish processes, like Zero Trust Security, to ensure users access only essential resources.
- Develop and regularly update an incident response plan to address and tackle cyber incidents.
- Perform security audits and vulnerability assessments to identify weaknesses in the network and systems.
Incorporating these measures will allow you to recover from potential incidents and minimize downtime, data loss, and financial impact.
Such techniques can help mitigate the impact of potential breaches for sustained business continuity.
Conclusion: Bridging the Gap to IAM Resilience
As the LAPSUS$ attacks have shown, no organization is immune to the sophisticated tactics of modern cybercriminals.
The Global Threat Report claims that 62% of attackers use legitimate credentials and built-in tools. These breaches often exploit vulnerabilities in various systems, with Identity and Access Management (IAM) systems emerging as critical gateways.
The exploitation of IAM systems highlights a crucial area of vulnerability that organizations must address to bolster their defenses.
This is where Acsense’s expertise becomes invaluable.
Our IAM Resilience Platform directly addresses the vulnerabilities exploited by groups like LAPSUS$.
By focusing on the critical intersection of backup strategies and IAM controls, Acsense offers a unique solution that enhances your organization’s ability to withstand similar attacks. Our platform ensures that your identity management infrastructure is not just a gateway for attackers, but a robust barrier against them.
With Acsense, you benefit from automated backups, comprehensive Point-in-Time investigations, and continuous data verification, all integrated within an IAM framework. This approach not only secures your data but also ensures that access to this data is continuously monitored and controlled.
In the face of threats that leverage weaknesses in IAM systems, Acsense transforms these potential points of failure into strengths, ensuring that your organization’s IAM infrastructure remains secure, compliant, and resilient.
Contact us to explore how Acsense’s IAM Resilience Platform can safeguard your systems against IAM vulnerabilities and provide robust defense against sophisticated cyber threats like those posed by LAPSUS$.
FAQs
Q. What is LAPSUS cyber threat, and how does it differ from other cyber threats?
LAPSUS$ is a cyber threat focused on data theft and extortion. The group has been conducting attacks globally on high-profile companies and government agencies.
Q. What are the primary targets of LAPSUS$ attacks?
LAPSUS$ is mainly focused on social engineering and stolen credentials. They target prominent and well-known gaming and software industries. Microsoft, Samsung, Okta and Nvidia are among their cyberattack victims.
Q. How does LAPSUS$ typically gain access to systems or networks?
LAPSUS$ gains access using basic techniques like stolen credentials for Remote Desktop (RDP) or cloud services such as Microsoft Office 365. In some cases, they impersonate employees and execute social engineering attacks.
Q. What are the common signs that indicate a potential LAPSUS$ cyber threat?
Unsolicited email or text messages with typos and errors, attachments, or links from an unknown person to employees or contractors are the primary signs of a social engineering attack. Such phishing attacks exploit human error to harvest credentials.
Q. Are there specific industries or sectors more prone to LAPSUS$ attacks?
LAPSUS$ targets many sophisticated companies with the apparent goal of gaining notoriety. The group mainly focuses on any company providing software, gaming, telecommunications, and other services.



